
SecureTower позволяет выявлять и блокировать майнинг криптовалюты на оборудовании организаций
Разработчиками Falcongaze подтверждена возможность использования SecureTower для выявления майнеров в корпоративных сетях организаций. В первую очередь такая возможность нужна для участившихся в последнее время случаев использования техническими специалистами и системными администраторами оборудования работодателя для майнинга криптовалют.
В SecureTower — системе предотвращения утечек данных и контроля сотрудников — давно реализован целый пласт различных функций, предназначенных для выявления нерабочей деятельности сотрудников за компьютерами. Список этих функций постоянно расширяется — в первую очередь в связи с новыми запросами заказчиков.
Нынешнее новшество связано со все чаще встречающимися новостями о сотрудниках различных организаций, которые начинают использовать корпоративное оборудование для майнинга криптовалюты. Подобная деятельность раньше была широко распространена на персональных компьютерах и «фермах» из нескольких видеокарт, однако из-за роста требуемых для добычи криптовалюты мощностей в домашних условиях стала практически бессмысленной. Другое дело — мощности доступные в организациях. У многих крупных компаний имеется большой парк рабочих машин и серверного оборудования, к которым имеют доступ системные администраторы и технические специалисты. Некоторые из них могут использовать его в личных целях и, в частности, все чаще используют его для майнинга криптовалют. Из-за подобной деятельности все больше организаций испытывают значительные убытки, связанные с повышением нагрузок на оборудование, его износом, повышенными счетах за электроэнергию. Благодаря технической подкованноcти таких работников, вывести их на чистую воду бывает весьма затруднительно.
Кроме того, опасность для организаций представляет вредоносное программное обеспечение, которое заражает компьютеры компаний с той же целью — использовать мощности оборудования для добычи различных криптовалют.
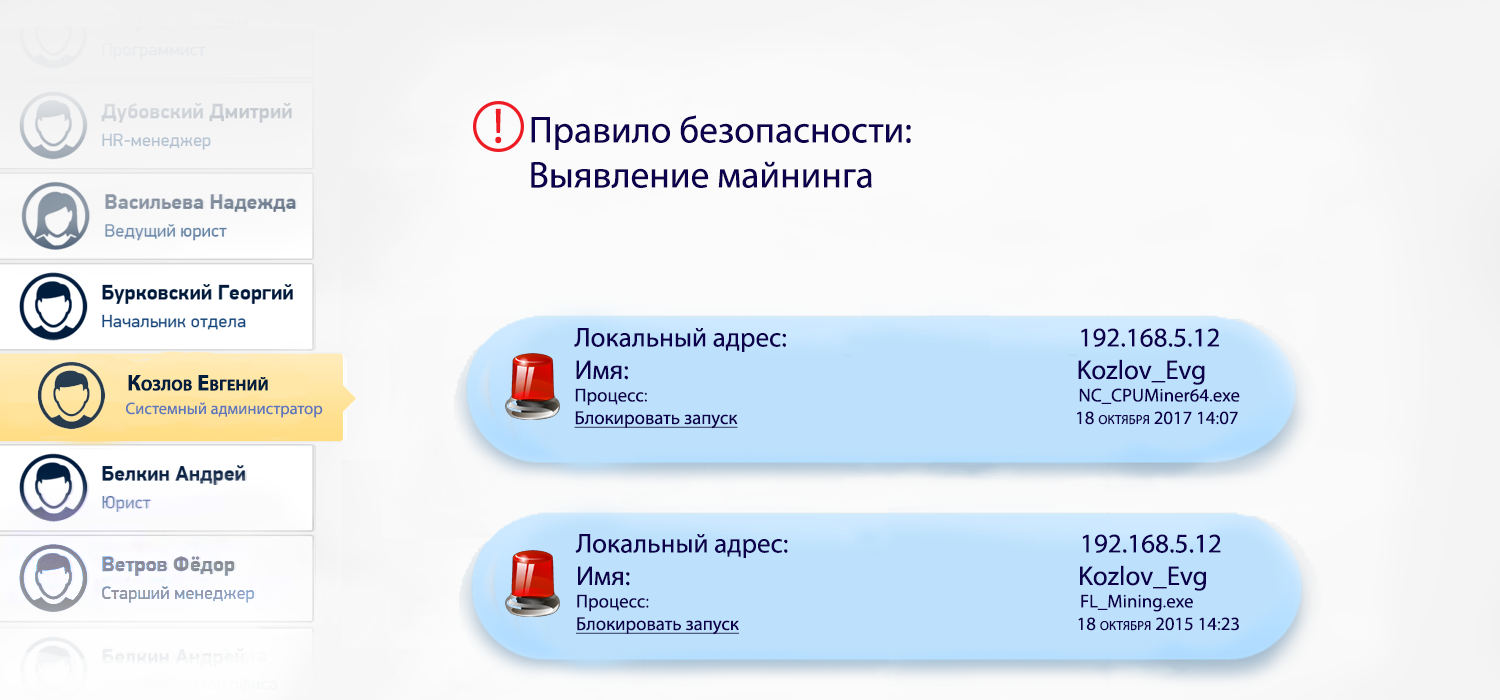
Выявить такую деятельность можно с помощью SecureTower. Детектировать активность майнеров в актуальной версии SecureTower можно с помощью специально настроенных правил. В этом случае агент SecureTower перехватывает активность процессов майнеров и, в зависимости от настроек, блокирует процесс либо уведомляет о нежелательной активности работника ответственного сотрудника.








.jpg)