

How to choose a DLP system?
How much profit do you lose on the fact that your employees divulge confidential information about your company? How many of them store sensitive documents in cloud storage or on insecure USB sticks? No one is safe from errors, but DLP systems exist to prevent them.
In a broad sense, the DLP system controls everything, creating a secure digital «circuit» of your organization’s internal network. Now, the protection of trade secrets is only one of the tasks set for DLP. Today, data leak prevention systems offer complete protection for your business from internal threats. It is understood that the software will not only help to accurately identify the source of the information drain and block it in time, but also to understand the causes of the incident by putting together a chain of previous events.
However, DLP is not an evidence collector, as it may seem, but rather a «mirror» that reflects all the processes and conditions of your organization. Control occurs by filtering and analyzing data intercepted from the corporate network. For this, agents are used, duplication of packets from one port of a network switch to another and integration with a corporate mail and proxy server. There is an opinion that agent interception is the most effective method of controlling information flows. Let's take a closer look.
How does agent interception work?
Pre-installed agents on each individual computer intercept all incoming and outgoing traffic, creating a single informational stream, carefully analyzed by the system in accordance with a given security policy. Agents can work both openly and in stealth, and the whole process can be compared with a conveyor belt, where the operator in real time rejects products, snatching them from the general flow of data. The system will respond to attempts by employees to bring information beyond the corporate network.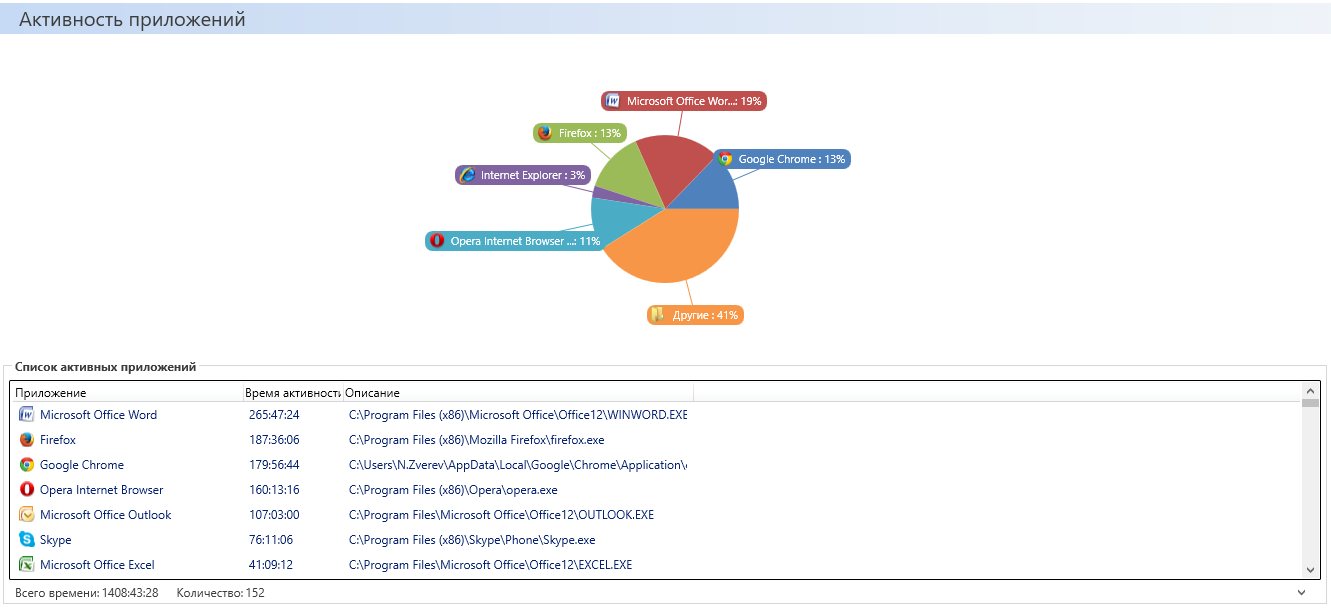
Which DLP system should I prefer?
When you choose a DLP system, pay attention to 6 principles:
- how many communication channels а product can control;
- reliability and speed of the system,
- analytical capabilities of software,
- qualification and efficiency of technical support,
- vendor reliability
- and cost of system ownership.
Principle 1 - control of information flows
The more communication channels the DLP system can control, the more valuable it is, so you need to understand exactly which of your employees use them for personal and corporate purposes. Integrated solutions in the field of information security control the reception and transmission of traffic of almost all email clients, such as «MS Outlook», «Thunderbird», «The Bat!», Including accounts in external mail services (gmail.com or mail.ru). They intercept text and voice messages of all modern instant messengers (Telegram, Viber, Skype or SIP), correspondence in social networks. In addition, files transferred to USB-drives, documents sent to print, web page traffic and so on.
Principle 2 - reliability and speed of the system
DLP should work in any networks without overloading them. A drop in the «speed» of the computer will cause suspicions among employees. The system should run smoothly in geographically remote networks on any number of computers. Pay attention to the support of mobile workstations, such as laptops and netbooks. The agent in offline mode must remove the same data as in stationary computers, and, after connecting the device to the corporate network, send the collected archive to the server.
Principle 3 - Product Analytical Capabilities
A DLP system must be able to:
- content (searches for specific words or phrases provided by the thematic dictionary),
- statistical (the number of sites visited, copied via USB files, etc.),
- event (launch of the application, transfer of the encrypted archive)
- and attributive (allows you to take into account the unique attributes of files, documents and devices) analysis.
In addition to them, the function of monitoring the employee’s network activity at the workplace is «embedded» in modern systems. In other words, you will be able to evaluate the effectiveness of employees using their working time and adjust the load. DLP becomes your HR consultant. It will provide you with a convenient systematic report on violations of labor discipline in general and for each individual employee in particular, even awarding the employee a risk factor. Often, DLP has an incident investigation function. You will be able to create a dossier for violators and collect the maximum information about incidents before responding appropriately. As a package of evidence, the system will provide a chronology of the employee’s actions at the workplace, his letters, correspondence in instant messengers, screenshots and webcam recording.

Principle 4 - qualification and efficiency of technical support
When purchasing a product, you should not be alone with the program. The task of technical support is to help in the implementation of the DLP system in the network of your company and quickly eliminate the difficulties that arise, improving the functionality upon request of the customer. Good tech support is required to understand the nuances of information security better than you do. Pay attention to how deeply experts understand the architecture of operating systems, the principles of protection and networking.
Principle 5 - vendor reliability
The difficulty is, when you first acquainted with the company, you can evaluate the vendor's reliability only by indirect signs: the number of offices, the technical staff, and the number of licenses. In addition, the manufacturer must have licenses for the technical protection of confidential information, the development and production of CIPS (confidential information protection systems).
Principle 6 - Cost of system ownership
It includes both the cost of the system itself and technical support. Correct DLPs are assembled on a modular basis, that is, as a kit, and the price may vary depending on the number of modules purchased, communication channels that you intend to control (or not control). After the system is configured, monitoring and analytical functions will fall on it, which will significantly save your money. This means that your business will require fewer security officers to oversee staff.
How to choose the best DLP system?
Choosing a Data Leak Prevention System is not a fast process. However, it should be understood that the time spent on finding the best DLP system that is right for your business would fully pay off in the future. When familiarizing yourself with vendors, compare the functionality of the products they offer.
- Make a clear technical task with a list of all communication channels that you want to control. Remember that modern DLPs, as a rule, have a modular structure, that is, they are assembled as a constructor from the required control options. DLP should never overload the system. Compare the offers of suppliers; determine how they will be useful to your business.
- Test software features as much as you need at the maximum number of workstations. Do not focus on a specific list of functions. Your task during this period is to understand how organically DLP has been introduced into the network of your organization and how effectively it controls information flows.
- Pay attention to the security and stress resistance of the system. Obviously, application security must be organized in such a way that an employee cannot remove it from the workstation. Burden DLP as soon as possible. Email newsletters from unknown sources, «merge» confidential documents, use «forbidden» words in the dictionary in controlled correspondence (such as: «salary», «customer base», «expenses», etc.). One unrecognized violation is enough to render the whole system useless.
- Do not refuse technical support services (especially since its participation in the life of your business was initially laid down in the bill). Check its efficiency, how deeply versed in safety issues, the qualifications of personnel. In the end, if something goes wrong, you will have to communicate with the support staff.
Get DLP, keep up with the times and do not worry about the information security of your business.







.png)





