

Information security: definition, requirements, models and stages
Table of Contents
For the last century society has experienced the most intense tech evolution breakthrough throughout history. And if before the word security was used in most cases to refer to physical violence and threats, now, with the development of technology it has changed the base definition. Information and sensitive confidential data became weapons, which can damage no worse than a sharp knife. So, the definition information security came into language and practice. What it is, which tasks it solves, and how to use it — this Falcongaze article aims to answer the main questions about information security.
Definition of information security
Information security is a set of measures and technical tools for preventing the spread of confidential information about society's facilities that can cause direct or indirect harm to their work. Such information may be presented by company measures to avoid competitive threats or deal with unscrupulous employees; secret technologies, government secrets, and personal data. All of that information can be used in unfair ways. Information Security is meant to prevent the spread of such information.
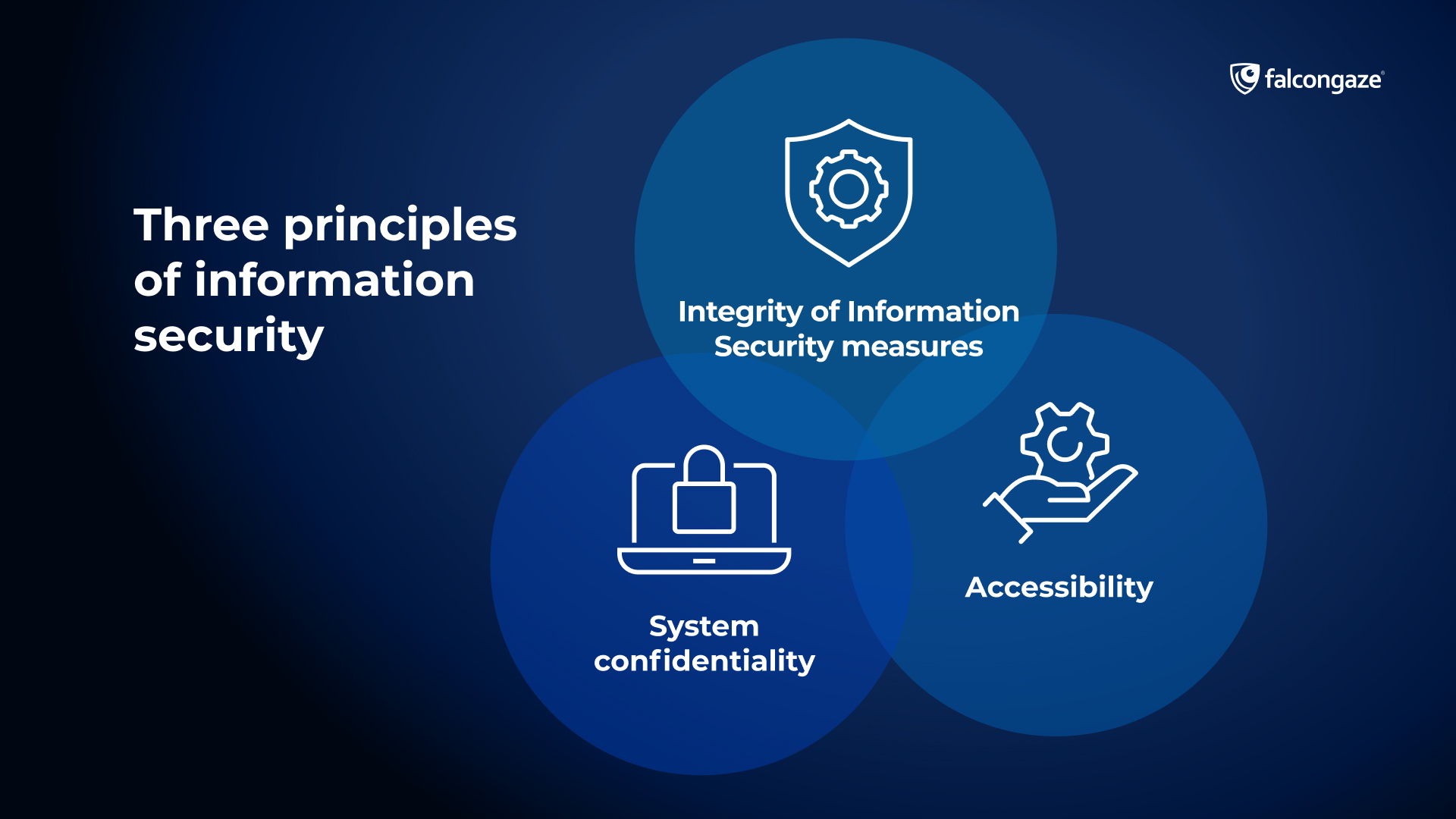
Three main principles of information security
Information security is based on three key principles, which allow to form a coherent approach to its implementation. The main principles are system confidentiality, integrity of measures, and accessibility.
System confidentiality
IS ensuring directly connects with interacting with sensitive confidential information and personal data. The entire data set should be treated with attention throughout the analysis chain. The analyzed information can only be viewed by subjects who have been authorized after verification and should remain private to all others.
Integrity of Information Security measures
This principle encourages to consider data security ensurement as a coherent process, with no exceptions or indulgences unless they are predetermined. This approach gives an impartial assessment of the state of affairs and also shows the real picture of what is happening.
Accessibility
It is a possibility for approved entities to get the access to any part of data, and the security services responsiveness to query processing.
What is information security even for?
Indeed, the main goal of information security is to ensure the safety of confidential information about a company, person, or state; and to level out the negative impact that can harm the company or individual. However, that doesn’t mean that every possible threat to data security has only a negative aim: to destroy the object of interest. It’s not always like this.
Information is frequently needed for analysis purposes: to compare competitors’ products with our own, to analyze the efficiency of business strategy, and to enhance internal company processes. Various sources can be used to get such information: employees of the company, documentation, intellectual property (inventions, utility models, industrial designs, patents, etc.), technical storage media, software, and others. The choice of source depends on the tools available, the objectives, and the potential usefulness of the data obtained.
Threats and risks to information security
A threat is a potential or actual action directed at causing material or moral damage to a company or individual. Naturally, in order to set up a data defense process, it is necessary to understand what risks and threats a company may face. Commonly, there are three main groups of threats:
Technogenic (related to the disruption of equipment or technologies of the protected system, also when using specialized hardware and software)
These risks may include the following:
- Usage of pirated software and circumvention of licenses;
- Malware implementation (viruses, encryptors, backdoors, blockers, mining programs, etc.);
- DDoS-attacks;
- Phishing;
- Physical and program audio and video surveillance, etc.
Here is an example of a threat to information security due to technogenic reason. For instance, Play’s ransomware attack on IT company Xplain in Switzerland caused damage to the local rail network and many of the state facilities. Hackers received in disposal more than 1,3 million files, among which 65 000 documents belonged to the Swiss Federal Government. Play managed to realize the threat to information security through phishing newsletters that contained malware.
Another example from 2010. At that time, the Win32/Stuxnet network worm had spread to a large number of private and public computer systems. This virus exploited Microsoft Windows system vulnerabilities (zero-day vulnerability), intercepting and modifying the information flow between Simatic S7 programmable logic controllers and SimaticWinCC (Siemens) SCADA system workstations. It went down in history as the first malware that harmed not only digital data but also caused real physical damage to equipment. The main source of the spread was infected USB drives.
Anthropogenic (related to the intentional or unintentional spread of confidential commercial data)
- Insiders leaks;
- Mistakes in the performance of official duties;
- Actions of unscrupulous employees.
One of the examples of an anthropogenic type of threat to company security may be the Colonial Pipeline case. It is the largest pipeline system in the USA and the main gas and oil vendor from the Gulf of Mexico to the entire East Coast. On the 7th of May 2020 in the Colonial Pipeline system, there was registered a case of ransomware infection. As became clear later, an attack was launched by hacker group DarkSide. Their aim was to get 5 million dollars of ransom. Even after the transfer of money, the company wasn’t able to quickly restore its business processes. It has led to large-scale crisis in several states and fuel shortages at the moment.
The guilty party from the Colonial Pipeline was one of the employees whose password was used in attack. Through this password to the VPN service, the hackers were able to gain access to the corporate system. The employee had previously used the same password to register another account, the information about which was already on the Darknet.
One more example: a hack of celebrities’ Twitter accounts in July 2020. Then hackers managed to publish the link to the message with the collection of cryptocurrency. The message was saying, “Send me 1 BTC and receive back 2." From that attack suffered accounts of Tesla and SpaceX CEO Elon Mask, Amazon founder Jeff Bezos, one of the largest private investors and head of Berkshire Hathaway Warren Buffett, ex-president of the USA Barack Obama, official accounts of Google, Apple, and many other companies.
As a result of the attack, nearly 300 people sent to crypto wallets a little bit more than 110 000 dollars. The situation also had a negative impact on Twitter itself: irreparable damage was caused to its reputation, and the price of stocks fell by 4.5%. The main source of information for the scammers was a Twitter employee who, in the words of the hackers themselves, “literally did everything for them.”
Natural (force majeure circumstances, natural disasters)

In what fields is information security the most important
It’s impossible to restrict the scope of information security. In some way, the unauthorized spread of information can damage every aspect of personal life, harm companies, and even harm governments. And still, we can allocate a few spheres where the use of data protection services is crucial.
- Critical infrastructure of the state and enterprises related to it. Energy, public safety, defense, and government facilities;
- Banking sector and financial organizations (the central bank, private and public banking institutions, pension and insurance funds, monetary organizations, etc.);
- Healthcare facilities;
- Transport and logistic complexes (auto, railway, water, air, and pipeline transport management systems);
- Facilities providing informational sovereignty (Notarial legal bases, information agencies and mass media);
As we can see, the need for information security exists in all the main areas of state and economic life. There is one rule to determine the need to use data protection services. Generally, this rule implies to legal entities (private or state), whose activities involve a large amount of sensitive confidential data as well as information that is constantly changing depending on external or internal factors (e.g., banks and exchange rates, airline and domestic schedules, railroad schedules, and so on). With such a scale of change, the main aim of information security is to track and prevent negative scenarios.
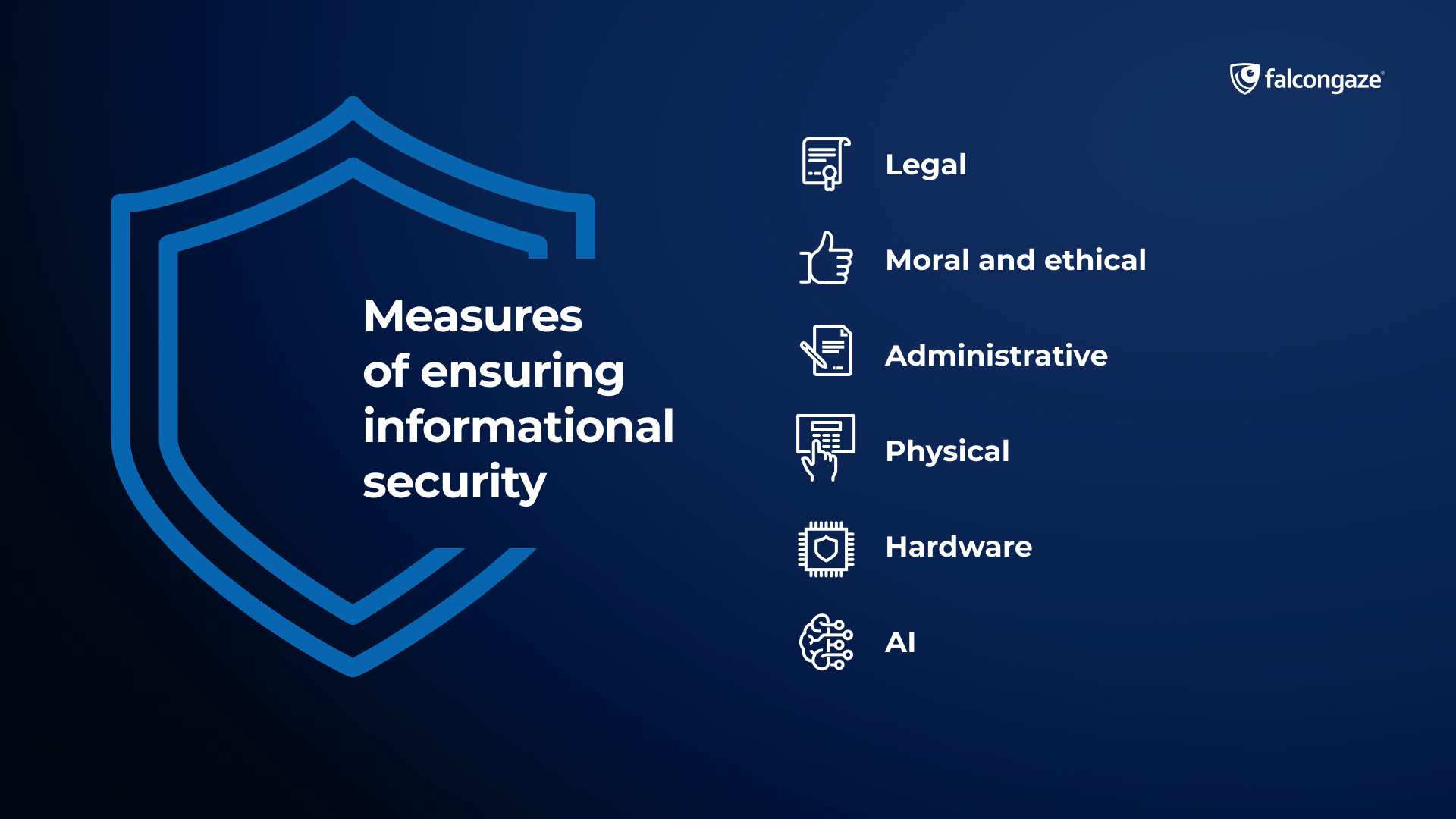
Which data protecting measures are used by IS professionals
It is commonly decided to allocate several types of measures that ensure informational security. Each of those measures ensures safety in its own segment of responsibility. However, it’s impossible to say that just one of those measures will be enough to prevent and eliminate potential threats to IS. One of the main principles of data protection is complexity. And the more measures a company or individual can include in their security system, the more reliable the entire protection system will be.
Measures of ensuring informational security divided into:
- Legal
- Moral and ethical
- Administrative
- Physical
- Hardware
- AI
Let’s talk about each of that measures.
Legal measures
It is the creation and adaptation of regulatory frameworks, international regulators, institutions, etc. to meet the needs of ensuring a comprehensive, effective, yet legal approach to information security. A lot of regulators today provide IS services even though they are not directly related to this sphere by their activities. The UN Security Council monitors the international agenda and can make recommendations on the implementation of IS systems to various nations. This also includes international product certification and standardization companies. For example, the International Consortium for Information Systems Security Certification (CISSP) and International Organization for Standardization (ISO) certifications are popular.
Legal measures also include the development and adoption of legal acts within the framework of state regulatory policies in this area, and the creation and optimization of licensing and IS management bodies in each country. For example, in the Russian Federation such bodies include the Federal Security Service of the Russian Federation (ensuring IS within the country), the Federal Service for Technical and Export Control (certification of IS protection means), the Roskomnadzor (tracking compliance of systems), the Ministry of Communications (development and implementation of regulatory documentation in the sphere) and others.
Moral and ethical measures
These measures may include written (codes of ethics, codes of conduct, etc.) and unwritten (personal moral qualities, internal standards of honesty, patriotism, duty) norms of regulating human behavior in a certain situation.
Administrative measures
Administrative measures of information security are steps to regulate processes, the use of labor and material resources, and the creation of a scheme of interaction between all participants in the information system. The goal of these measures is to create reasonable and understandable rules of behavior directed to prevent risks for IS. An example of such a measure is a trade secret agreement in the company (prior to informing the employee of the responsibility for possessing information within their competence).
Physical measures
Actual physical reaction to disruptions: lock and safe installation, access control systems, video surveillance, etc.
Hardware measures
It is an intermediate stage between physical protection and software protection. Hardware measures, like software measures, become part of the system. They can be tools to protect speech information (white noise, audio) or electronic devices to prevent unauthorized access (USB identifiers, electronic keys, hardware firewalls, etc.). But at the same time they use mechanical capabilities to counter potential threats, they are independent physical objects that can be quickly removed from the protected system.
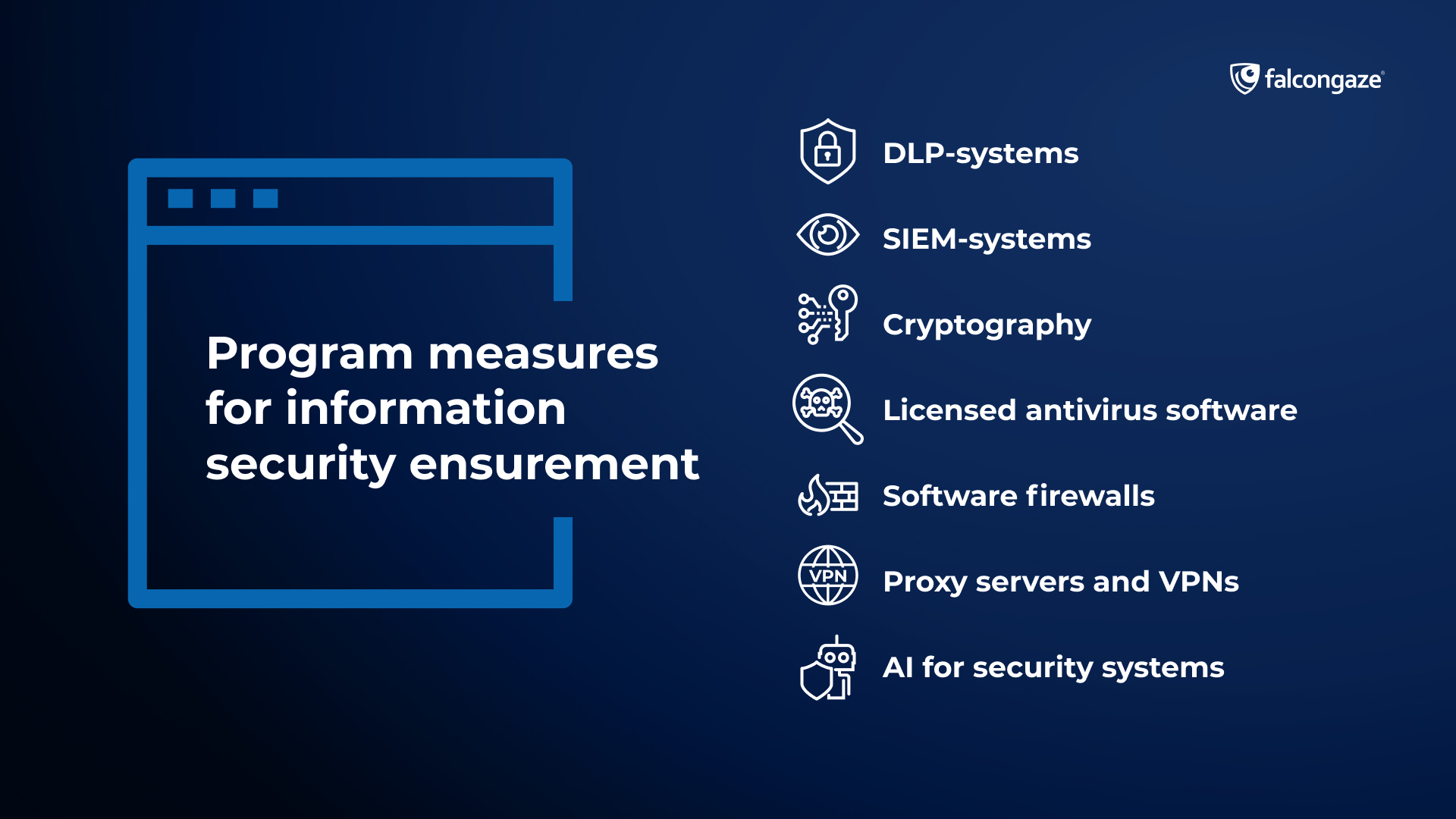
Program measures
Program measures for ensuring information security are aimed at the execution of three main functions: identification of objects, authentication of system participants, encryption and data processing.
- DLP-systems (Data Leak Prevention) ensure the prevention of data leaks outside the company's outline and monitor personnel for intentional or unintentional disloyal behavior. An example of such a system is SecureTower from Falcongaze. The advantage of SecureTower is its availability for free use for 30 days. Read more at the link.
- SIEM-systems (Security Information and Event Management). As it is clear from the name, this program solution is to analyze all network activity and real-time reaction to potential threats and cyberattacks. Examples of SIEM-systems: HP ArcSight, IBM QRadar SIEM, McAfee NitroSecurity, and others.
- Cryptography. It is a set of operations on text encryption that allow to save all information in the system, changing its appearance. With the help of cryptography, confidential information becomes unavailable to a potential attacker, it cannot be read without a special decryptor. There are two generally recognized systems of cryptography: traditional symmetrical crypto systems, in which encryption is accomplished by one secret key; and asymmetrical crypto systems use many keys to encrypt and decrypt messages.
- Licensed antivirus software. Among them are Norton Antivirus, Bitdefender, TotalAV and Intego.
- Software firewalls that act as a filter between the Internet and the local network of a specific company. They block incoming traffic according to predetermined rules. Examples: ZoneAlarm Pro Firewall, Comodo Firewall and others.
- Proxy servers and VPNs. These two technologies are similar. They are both aimed at replacing IP addresses with their own and masking the real traffic. They differ mainly in the cost of implementation and the presence of crypto-encryption (VPN). Examples of proxy servers are CoolProxy (Windows), ICS (Linux), as well as VPN services NordVPN, TunnelBear and others.
AI for security systems
In the modern world cybercriminals learn and adapt faster than a weapon against them is created. Only self-educating mobile systems such as artificial intelligence (AI) are able to keep up with all the changes. AI development has peaked in the last two years. And if most recently AI was just a support tool in the general complex of IS measures, then now it is a full-fledged solution to prevent leaks.
Examples:
- CrowdStrike Falcon. A security solution based on AI that uses machine learning, behavioral AI and a special language model for endpoint protection, threat detection and incident response in real time. CrowdStrike Falcon integrates antivirus (AV), endpoint detection and response (EDR) systems, and a 24/7 managed search service in a single agent.
- Vectra AI Attack Signal intelligence combines AI, data processing and machine learning to detect cyberattacks in real time.
- Fortinet FortiGuard is a system based on AI that combines threat analysis in real time with global protection to detect and block complex attacks.
Legal aspects of information security regulation
The modern state in general has set its attitude toward information security. This term is given a legal definition, the sequence of ensuring, auditing and responsibility for its observance by the participants in society is established. We suggest reviewing the main legal acts using the examples of Great Britain, the European Union, the United States of America and Australia.
Great Britain
In the UK, data protection is governed by the UK GDPR (General Data Protection Regulation) and the DPA (Data Protection Act) 2018.
GDPR (General Data Protection Regulation) determine how organizations should process personal data. After Brexit, there is two versions of this document: UK GDPR and EU GDPR. These documents are quite similar, and UK GDPR is supplemented by DPA - Data Protection Act, about which we’ll talk a little below.
The UK GDPR is based on six main principles: lawful processing, data subjects’ rights, valid consent, data protection by design and by default, transparency and privacy notices, international data transfers, mandatory data breach notification, DPOs (data protection officers). Document applies to UK organizations that collect, store or otherwise process the personal data of the UK residents, as well as to non-UK organizations.
In UK legislation suggests the existence of controllers and processors; both can be represented as a person or legal entity, public authority, agency or any other body. Data controllers determine how and why personal data is processed, and data processors – process personal data.
One of the notable features in UK legislation is division of personal data into two groups: personal data itself and sensitive data (Special categories of personal data). It is said that the second group of data is putted under much stronger control in terms of GDPR.
The next important document is DPA 2018 (Data Protection Act 2018). This UK law sets out how personal data must be collected, handled and stored. It also gives every person the right to know what personal data is held about them and to have that data erased in certain circumstances.
UK DPA 2018’s main provisions are as follows.
- Part 2, Chapter 3 sets out exemptions for manual unstructured processing and for national security and defense purposes.
- Part 3 sets out the regime for processing personal data for law enforcement purposes.
- Part 4 sets out the regime for processing personal data by the UK’s intelligence services.
- Part 1 contains preliminary information, Part 5 deals with the powers of the Information Commissioner, Part 6 covers enforcement and Part 7 provides supplementary information.
These are two main legislation documents - UK DPA 2018 and UK GDPR - which regulate the data security in Great Britain.
Another important legal acts:
- Privacy and Electronic Communications Regulations 2003 (PECR) sit alongside the UK GDPR and the DPA. It provides a set of specialized rules.
- The Retained EU Law (Revocation and Reform) Act 2023 (REULA). The aim of the REULA is to make clear specified EU laws that were retained as part of UK law after Brexit. The REULA determine how data protection law is interpreted and applied by the courts. It abolishes the principle of the supremacy of EU law, which means that any retained EU laws (such as the UK GDPR) have to be interpreted in a way that is compatible with domestic law.
- The PECR (Privacy and Electronic Communications (EC Directive) Regulations 2003) set out privacy rights in electronic communications.
- The EU-UK Trade and Cooperation Agreement dated 31 December 2020 (the TCA) allow data transfers from the EEA to the UK to continue unrestricted for an interim period.
One of the main controlling body responsible for overseeing the UK GDPR in the Information Commissioner’s Office.
European Union
- The Digital Services Act (Regulation (EU) 2022/2065
The DSA applies to a wide range of companies providing Internet services. It requires online intermediaries to identify and promptly remove illegal content, restricts the use of interfaces that can mislead users, and strengthens protections for children, who spend significantly more time online than ever before.
- Cybersecurity Law
The Cybersecurity Act significantly strengthens the EU Cybersecurity Agency ("ENISA"), giving it greater responsibilities and at the same time greater powers. ENISA's tasks include strengthening co-operation in the EU, assisting Member States in combating cybercrimeu. ENISA also supports and co-ordinates the actions of EU member states in the event of large-scale cyber attacks.
- European General Data Protection Regulation (GDPR)
This document is one of the most important data protection laws in the EU. The GDPR standardises data protection regulation in the EU, defines what constitutes personal data and privacy, and simplifies data protection regulatory processes for international organisations.
- Network and Information Systems Directive (NIS Directive)
Alongside the GDPR, the Network and Information Systems Security Directive (NIS Directive) is an important piece of legislation for the financial sector. The NIS Directive was the first ever EU cybersecurity and resilience directive adopted to improve cybersecurity across the EU.
- Convention on Cyber Security (2001)
The adoption of the convention united the efforts of EU member states in the fight against cybercrime. The provisions of the Convention serve to co-ordinate and provide assistance: technical, expert and information knowledge that can be utilised in the event of a critical cybersecurity situation. This instrument provides for a comprehensive criminal law policy for offences related to information technology, personal information, etc. The Convention classifies the main types of offences in the cyber environment; special attention is paid to the procedure for international cooperation in the field of information security.
USA
Here are a few U.S. laws that govern information security:
- FPA: Privacy Act of 1974
The FPA regulates the collection, storage, use and dissemination of personal information that is kept on federal systems. The document forbids the disclosure of such information from systems controlled by a federal agencies without the written consent of the person to whom the data belongs. The exception is cases provided for by law - there are 12 such situations described in the law.
The law gives people the ability to seek access to and changes to their records and sets various requirements for how the agency records data.
- The Gramm-Leach-Bliley Act (GLBA)
The GLBA applies to financial institutions (insurance companies, banks, auto dealers, securities firms, etc.) - the list of companies is quite wide. The document requires organizations to “develop, implement and maintain a comprehensive information security program, structured in one or more easily accessible parts and containing administrative, technical and physical security measures commensurate with the size and complexity of the organization, the nature and scope of its activities, and also the sensitivity of any customer information." Under the Privacy Rule created by this law, financial institutions are required to take measures to protect consumer rights.
- COPPA: Children’s Online Privacy Protection Act
COPPA applies to websites and online services whose audience and users include children under the age of 13. The law regulates how websites for children collect, use and/or disclose personal information from children who use such online services.
- ECPA and SCA: Electronic Communications Privacy Act and Stored Communications Act.
The Electronic Communications Privacy Act (ECPA) and the Stored Communications Act (SCA) are privacy laws. These documents were originally developed and adopted to limit the surveillance of citizens - today the ECPA and SCA prohibit the intentional use, disclosure or unauthorized access to any wire, oral or electronic communications. It means that emails, phone talks and data stored on computers is protected and cannot be disclosed without permission. At the same time, not all of that data considers by law as equal. For example, if disclosure is needed, some information may be obtained from subpoena; other information requires a special court decision; another information requires a search warrant.
- HIPAA: Health Insurance Portability and Accountability Act
The law is exclusively related to the healthcare sector and regulates the protection of confidential medical information. Without the patient’s consent, data about their health stored in the systems of medical institutions cannot be disclosed. At the same time, medical information may be shared to provide health care and protect the welfare of the public. As with other examples of legislation that have already been mentioned, exceptions are possible.
Now HIPAA is a set of rules (Privacy Rule, Security Rule, Breach Notification Rule, Omnibus Rule, etc.). For companies providing information security services, the HIPAA Security Rule is of particular importance in this regard, because It is in this section of the document that the safety measures that a medical institution must comply with are outlined.
In the United States, along with federal laws, other documents may be applied; law enforcement practice differs. Laws and documents governing the protection of personal data may vary from state to state.
Australia
Australia's information security laws govern the storage and processing of personal data in areas of public life such as privacy, government, healthcare, telecommunications, video and audio surveillance, freedom and accessibility of information and much more. The legislative framework can be called broad and well-developed. Let's look at the most important documents and their provisions.
- Privacy Act 1988
This document defines how businesses and federal government agencies must handle personal information. The Act sets out 13 Privacy Principles (APPs) – the core tenets on which Australia's information security is based.
- Crimes Act 1914 (Cth);
The law defines and establishes penalties for the most serious federal crimes, including crimes committed in the cyber environment against information security.
- Security of Critical Infrastructure Act 2018 (Cth) (SOCI Act);
SOCI protects information about critical infrastructure assets. This means that it is an offense to disclose information about these assets, even if you are the responsible person.
- Telecommunications (Interception and Access) Act 1979 (Cth);
The TIA makes it an offense to intercept or access private telecommunications communications without the knowledge of those involved in those communications. The TIA authorizes access to such content when necessary for law enforcement and national security purposes.
- Information Privacy Act 2009 (Qld)
The law states that individuals have the right to have their personal information collected and processed in accordance with certain rules. Companies are required to collect and store only the information that is directly necessary for their activities. This legal entity must ensure that a person can easily find out what information it holds about them and how he uses it. If a person asks, a company must give them access to their personal information and allow them to make changes to it, as long as it is not contrary to the public interest.
- Personal Information and Protection Act 2004 (Tas)
The purpose of this document is to protect the privacy of individuals by controlling the ways in which the government may collect, store, use, and publish records containing sensitive personal information that clearly identifies an individual. The law also gives individuals the right to access this information, which may appear in various types of records, including, for example, case files and patient records maintained by the Department of Health, Human Services and Justice, etc.
Issues of IS
Obviously, such a mobile environment as information and its security have a number of problems. Let’s discuss those problems.
- Data Abundance
The first issue is that the amount of data needed to be protected is only growing. Every year the amount of information used is growing, the volume of business correspondence increases, people are more and more communicating through social media, apps and services that are used in every aspect of one’s life and business activities. Every year volume of online communication is growing by hundreds of percent, and so that information needs to be protected. To meet that need IS tools are being adapted, but their adaptation is not always successful in direct proportion to the growth of data volumes.
- Law
Today every government, every company and every person remain alone with the problem of making their environment safe. There is no one approved approach to IS and so there is no general legislation that could solve that problem.
- Criminals
Along with data volume growth, the number of ways it can be leaked or maliciously externally injected also increased. Cybercriminals adapt much faster than products that ensure security. An example is near: malware based on AI already exists.
Conclusion
Information security is a set of measures. It’s impossible to create a working IS tool without taking into consideration the comprehensiveness and complexity of this task. Each object: government, company, a person can freely choose their way of protecting information. But the one thing remains solid – in the modern world no one can ignore the question of information security.







.png)





