

What is DLP systems?
Table of Contents
Data Leak Prevention is a specialized software, which protects organization against data loss. This technology grants both blocking of confidential information transfer through various data channels and monitoring employee activity. Therefore it allows to find vulnerabilities beforehand.
Why does company need DLP and how does the solution work?
Companies often pay more attention to external threats such as spam and phishing attacks, denial-of-service attacks (DoS attack), viruses (Trojan, worms), fake web pages, spyware and adware, social engineering. But frequently, internal threats rather than hackers are far more damaging for companies. In theory, any employee can be a potential insider and endanger information security. No one is immune from malicious intent or trivial mistake: both low-level managers and top management.
The principle of DLP operation is simple and consists in analyzing all the information - outgoing, incoming and circulating within the company. Solution identifies information via algorithms. If the data is critical and goes where it is not supposed to - DLP blocks the transition and/or notifies officer-in-charge.
DLP is based on a set of rules. They can be of any complexity and are related to different aspects of employee activity. If someone breaks them, then security officer is notified.
For example, security officers identified an employee who mined cryptocurrency in a company X. This was detected via user activity module. The report revealed the workstation did not turn off at night. The officers looked through the history of running processes and turned out the employee had started the mining process before leaving.
DLP keeps tracking not only work time and running programs but any interactions with data. Among such actions are keyboard input, correspondence, email file transfer, instant messengers and social networks, document printing, idle time, SIP telephony, web activity etc.
Ways to intercept data
In order to analyze data DLP must get it.
There are two main ways to intercept data: server-based and agent-based traffic monitoring. In the first case, DLP controls network traffic on the server responsible for endpoints interactions with the outside world. In the second case, IT officer installs to all endpoints specific program modules (agents), which transfer data for analysis from each PC to DLP servers.
Agent-based interception is more common. It lets to obtain much more data from various communication channels, therefore prevents leaks better.
Does your organization need DLP?
Each company owns valuable information, which may attracts intruders both from the outside, and from the inside. Such information may include a customer database, specific features of technological processes, drawings, etc. Even a trivial press release sending base carries a competitive edge, which you hardly want to give competitors.
How to choose DLP?
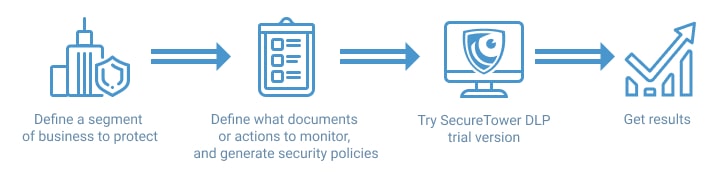
If you've realized that you need a data protection solution, the question is how to choose it among the product variety. First, ask yourself a few questions:
What data transmission channels do you want DLP to control?
What tasks do you want DLP to perform i.e. incident investigation or just traffic interception?
What budget are you ready to allocate for DLP?
In order to answer correctly all three questions it would be useful to request a demo version of software. Most companies-developers give such opportunity. It will allow you to see how the particular DLP works. During the trial period you will understand chosen software pros and cons and will have probability to compare it with others.
DLP and privacy
DLP itself if properly implemented will not violate any rights. Software monitors only workflow, not private life.
Implicit ways of using DLP
It would seem the solution designed to control data leakage could not provide your company with other benefits. However, modern DLP has some advantages not obvious at first glance.
Many DLP solutions are able to track employees' working time. Each user's workflow is displayed in a form of statistical report, what allows you to evaluate employees’ involvement in the business process.
DLP is aimed not only to prevent leaks, but also provide evidence of malicious activity to court if any.
When employees realize that their activity is monitored, more responsible attitude to job arises. That leads to better team environment.
DLP technology ensures the safety of all company information. It keeps in its storage all employees' communication and grants access if necessary.
-
Staff workload analysis
Many DLP solutions are able to track employees' working time. Each user's workflow is displayed in a form of statistical report, what allows you to evaluate employees’ involvement in the business process.
-
Providing legal support
DLP is aimed not only to prevent leaks, but also provide evidence of malicious activity to court if any.
-
A tool for motivation
When employees realize that their activity is monitored, more responsible attitude to job arises. That leads to better team environment.
-
DLP as storage
DLP technology ensures the safety of all company information. It keeps in its storage all employees' communication and grants access if necessary.






.png)





