

What is UBA?
Today business faced with challenge of internal threats anticipation. It is impossible to foresee the future. However, you can build a forecast based on analytics. User behavior analytics (UBA) is a useful tool for this purpose. UBA improves cybersecurity infrastructure via detection of internal threats, targeted attacks and financial fraud.
- Risk analysis
UBA technology analyzes history of user activity at working place. Thus, normal and malicious patterns of user behavior are determined. UBA provides security officers with necessary data for understanding of user behavior patterns.
- Data integration
UBA technology allows to work with various data types, such as users positions and titles, level of access, accounts and permissions, user activity and geographical location, as well as security alerts. These data can be identified by past and current activities. Besides, the analysis takes into account such factors as used internet resources and duration of sessions. Indicators are automatically updated when changes are made to the data.
- Prioritized data visualization
UBA technology does not highlight all anomalies as risk. Instead, the potential negative impact of user behavior is evaluated. If the affected data is not sensitive, the incident get low level of risk. If the violation of the adopted security policies is connected with something more sensitive, for example, with personal data or trade secret, the incident will receive a higher risk assessment. Thus, security specialists can prioritize the necessity of their actions.
With the help of machine learning algorithms UBA-systems can decrease quantity of false alerts and provide more clear and accurate information about risk.
Why does your business need it?
- It helps enterprises and companies to detect internal threats, targeted attacks and financial fraud.
Human factor as previously remains the primary threat for any kind of business. The UBA system considers patterns of human behavior. Using computational algorithms and statistical analysis it reveals significant anomalies of these patterns, which carries potential threat. Instead of collecting information about gadgets and events, UBA focuses on people, using these gadgets.
- It optimizes work of information security officer and neutralizes possible mistakes related to human factor.
Security systems collect huge amount of various data, therefore manual analysis of them may take years or even decades. Besides, there is no clear understanding, what particular data foreshadows potential attack. UBA solution focus on behavioral patterns and their violations, which are bright markers of increasing risk. Security service receives visual reports, containing average risk level in company and separated TOP-list of most unreliable employees. With this information, the security officer can carry out preventive work in a timely manner and neutralize the existing risk.
How UBA technology is represented on the market?
Today there are various solutions that make it possible to use UBA technology. With their help, you can conduct in-depth analytics, build patterns of users behavior and prevent possible threats. However, due to the high cost of such solutions, companies prefer combined functionality. For example, UBA fetures integrated with DLP system or employees control system.
UBA and Falcongaze SecureTower
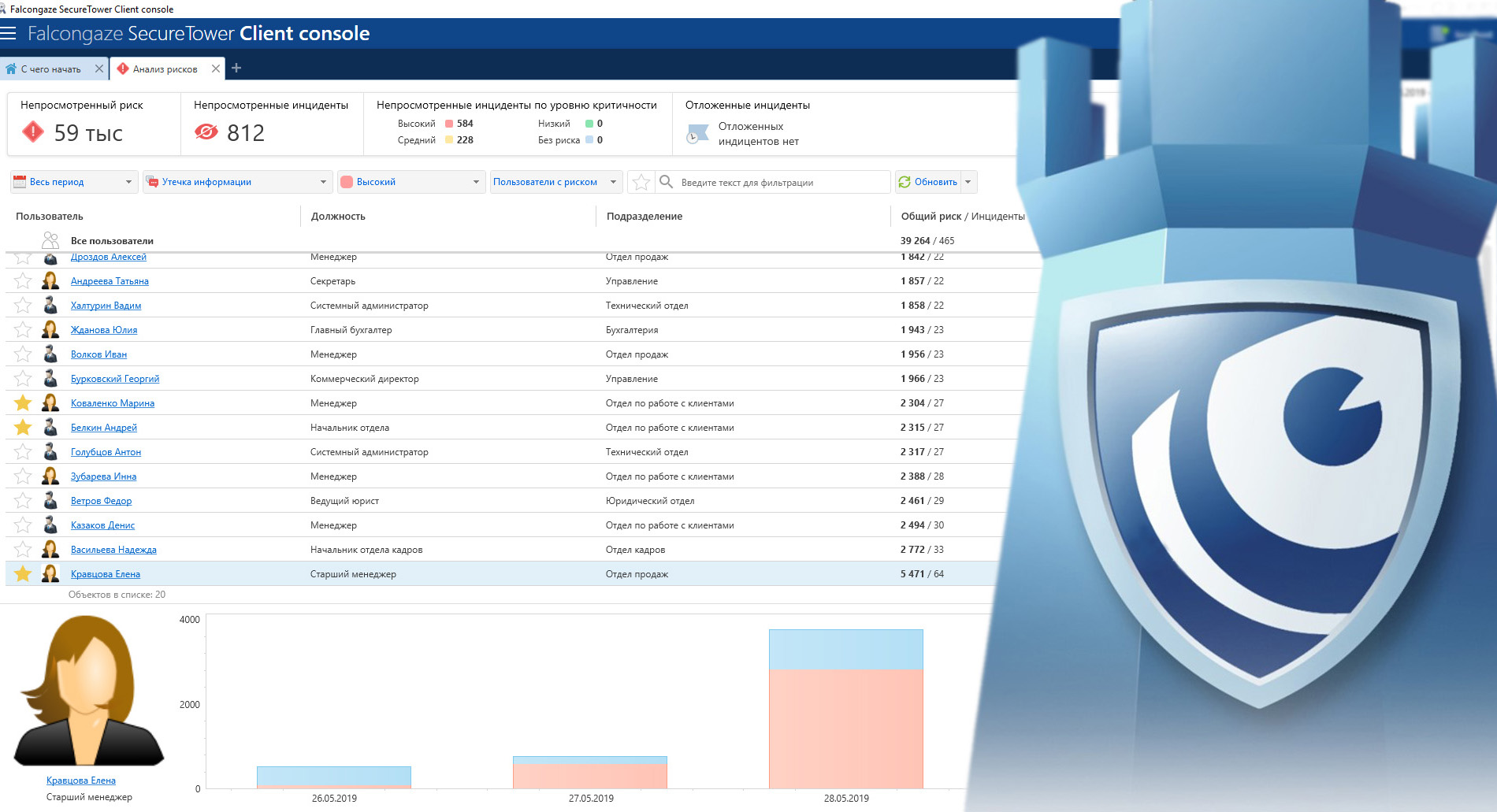
In the latest version of SecureTower was added UBA-module Risk analysis. It allows to monitor abnormal and potentially dangerous for organization changes in employees behavior.
The module identifies total level of risk coming from employees, based on incidents. Information security officer can configure the level of risk for each specific incident. As a result, a TOP-list of employees representing an increased threat is formed. Changes in risk levels are automatically reflected in the dynamic graph of employee temporal trends.
Risk analysis module automatically generates all the necessary information and reports to carry out research of trends in user behavior.






.png)





