Configuring a security rules to identify cryptocurrency miners on workstations
Creating a security rule
In order to create a security rule in order to identify the miners processes, you need to perform several steps:
1. Start the client console and go to the Security Center.
2. Add a new "General" security rule:
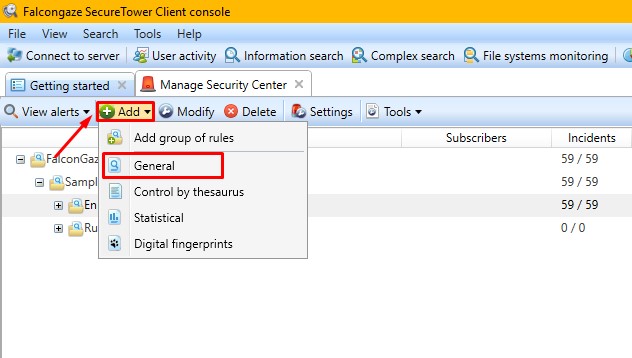
3. Toggle the radio button to the "or" block
4. Specify the operation type "Process - File name - Contains":
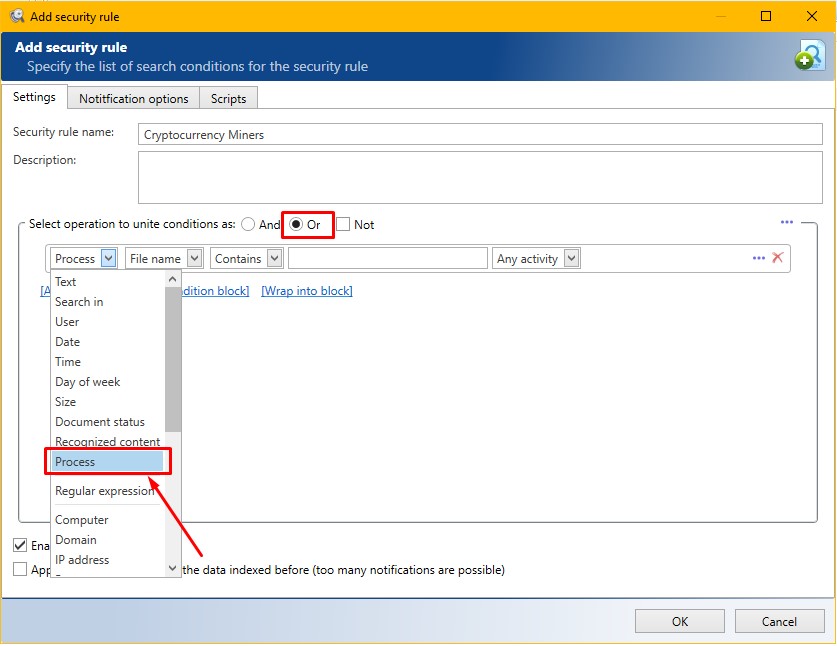
5. Specify the name of the process-miner and click "Add Condition":
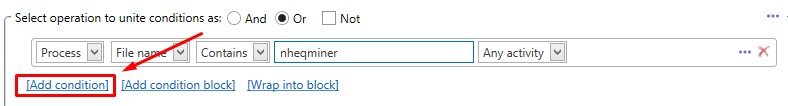
6. In a similar way, indicate the names of the necessary processes *. For example:
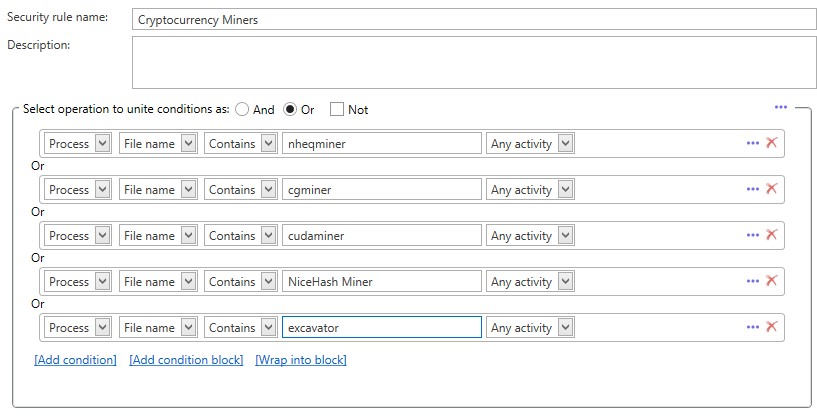
7. Click "OK" after adding the required process-miners.
Note: "*" and "?" characters are allowed. For example: "Process - File name - Contains - *miner*"
* - The list of the most popular miners: ccminer.exe, cgminer.exe, cudaminer.exe, EthDcrMiner64.exe, ethminer.exe, excavator.exe, gominer.exe, GUIminer.exe, miner.exe, nheqminer.exe, NiceHash Miner 2 .exe, NsCpuCNMiner64.exe, NsGpuCNMiner.exe, PascalCoinMiner.exe, sgminer.exe, xmr-stak-cpu.exe, ZecMiner64.exe.
