Try out new features
- The Agents Proxy server added
Agent Proxy server has been added, which is responsible for maintaining agent network connections and sending data to the Central Server. In addition, the tasks of the Agent Proxy server are to store agent configuration files generated by the Agent Control Server and Active Directory schemas (if available). Adding a Proxy server is implemented by means of its allocation from the Agent Control Server as a separate service.
This solution made it possible to optimize a) the process of data exchange between the agent and the server and b) the load on computing and network resources.
Due to the modifications in the Agent Control Server architecture, a significant redesign of the Agents module took place. Following settings are on the designated tabs:
- Endpoint Agent control settings.
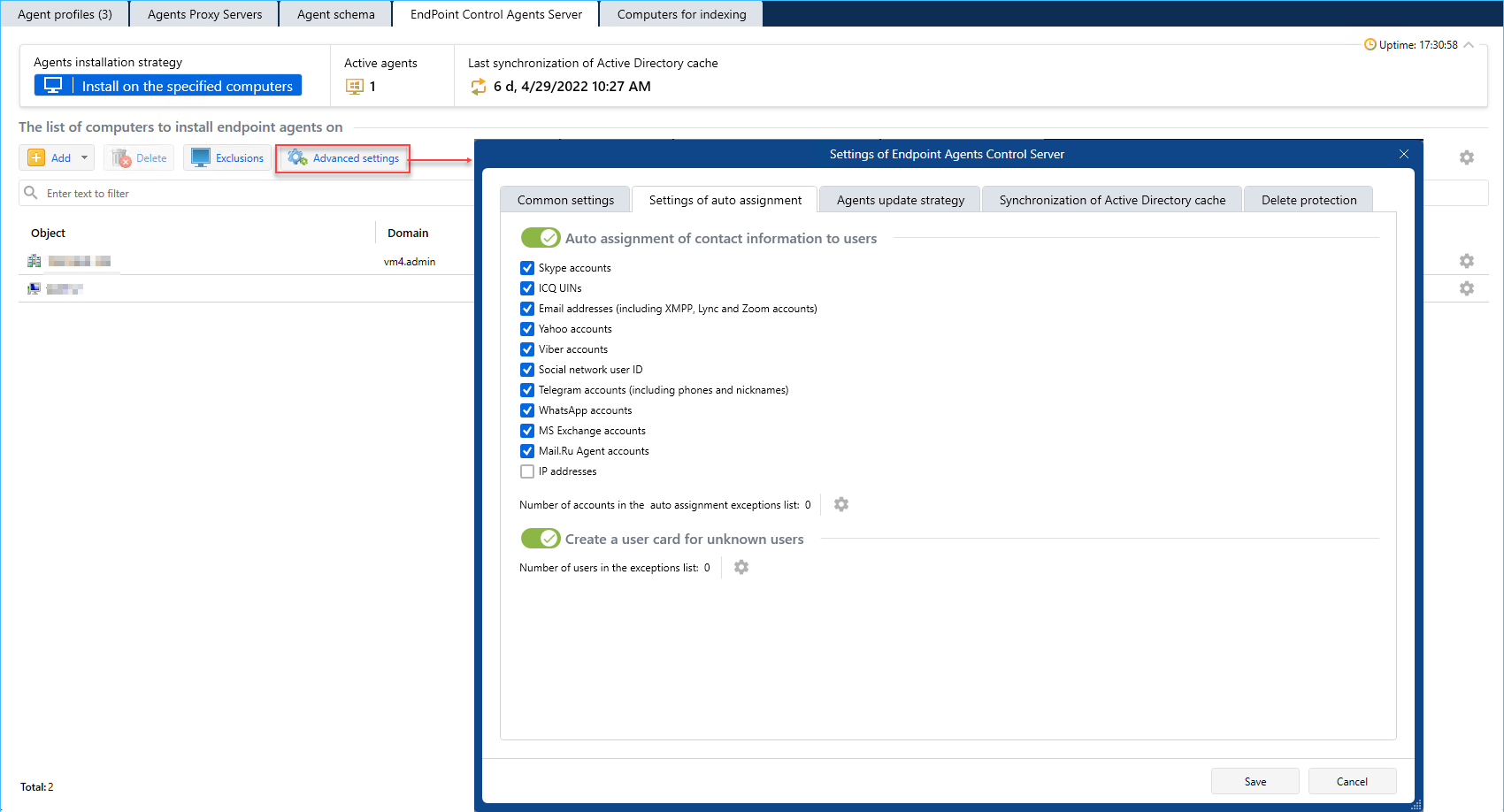
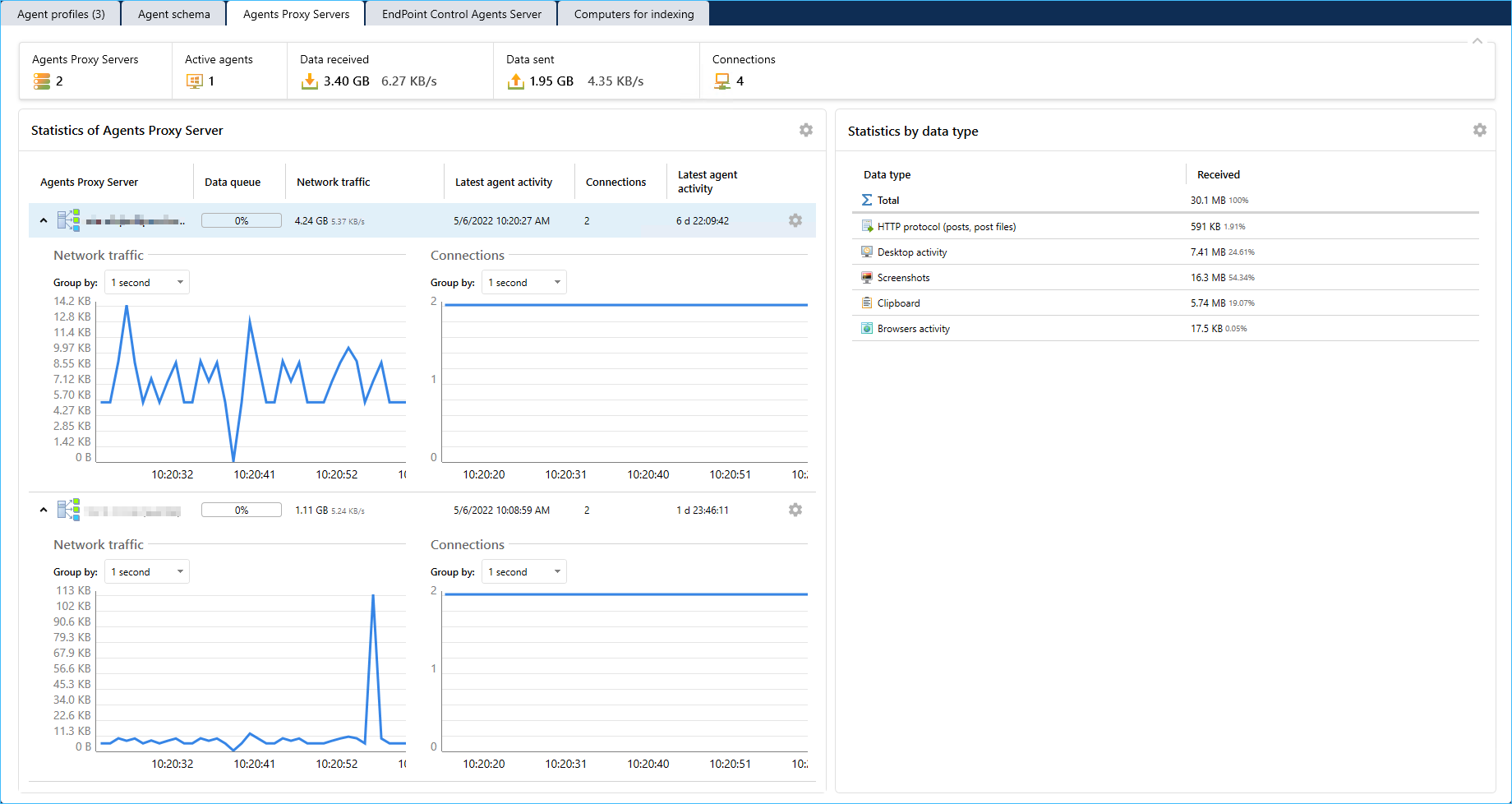
- Agents proxy server settings.
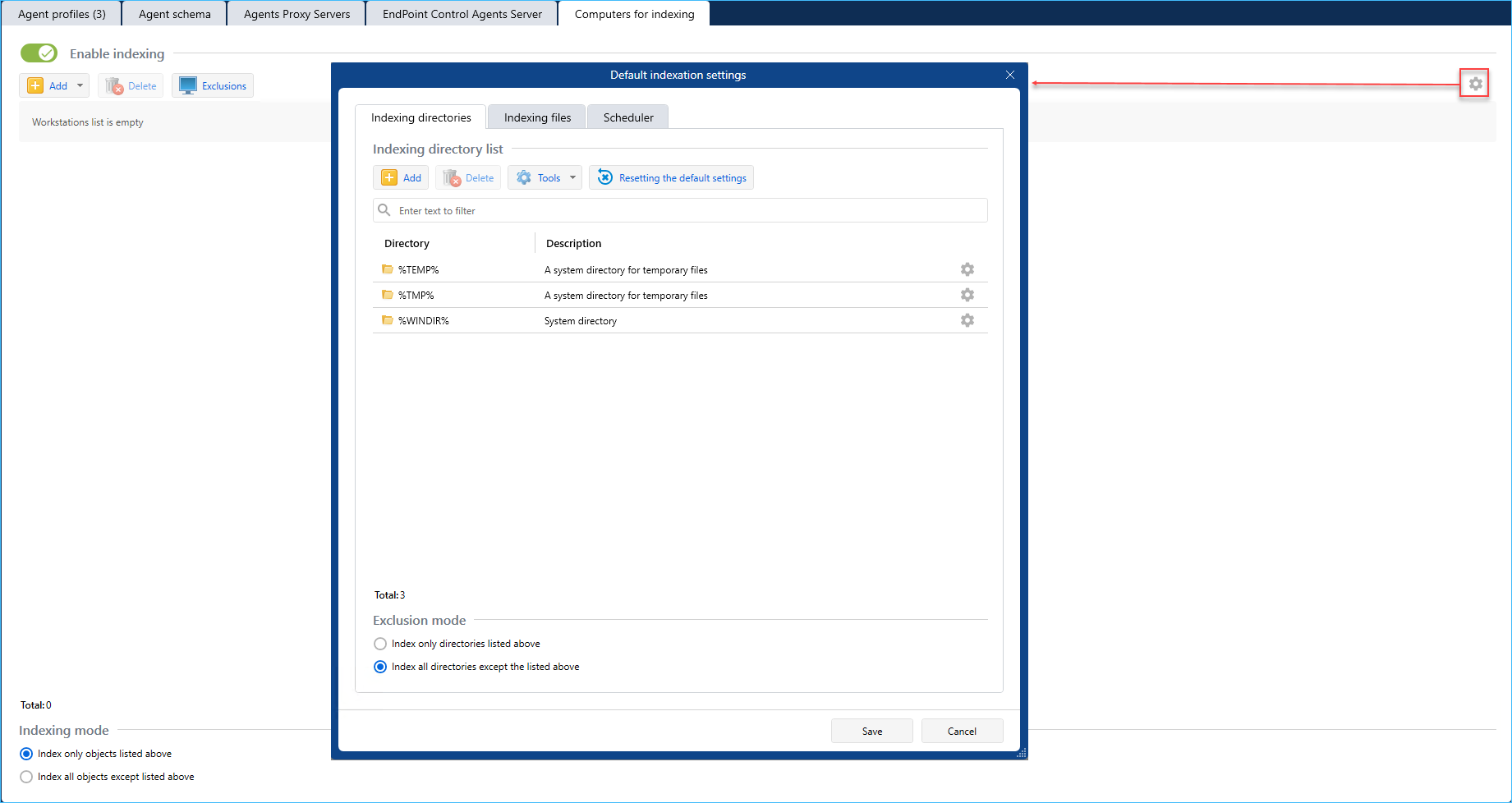
- Workstations indexing settings.
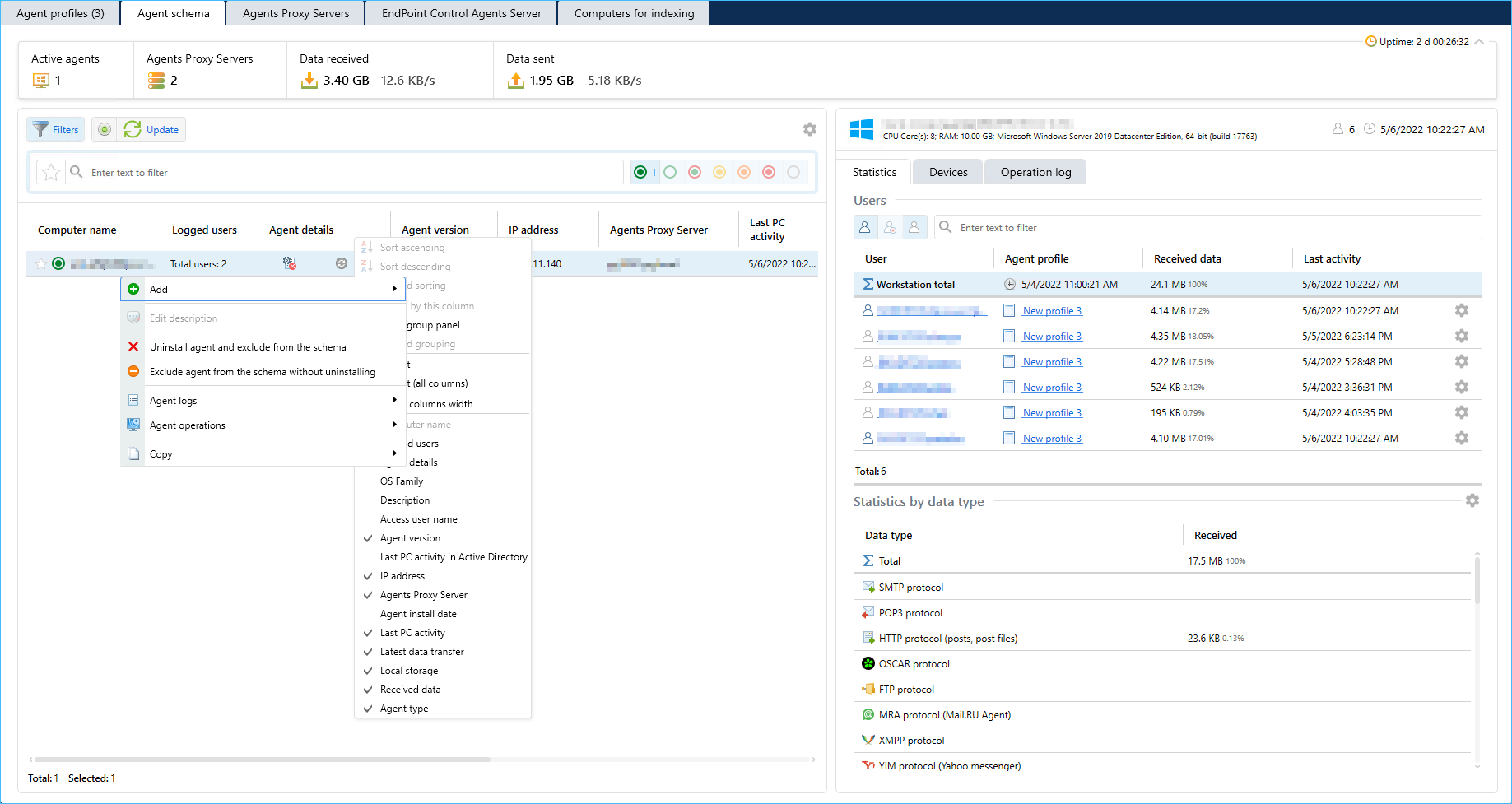
- Agents schema tab usability improved.
- On the Agents Proxy server tab, you can manage the Agents Proxy server service settings, monitor data transfer statistics (optional), configure data transfer queue and data transfer scheduler settings.
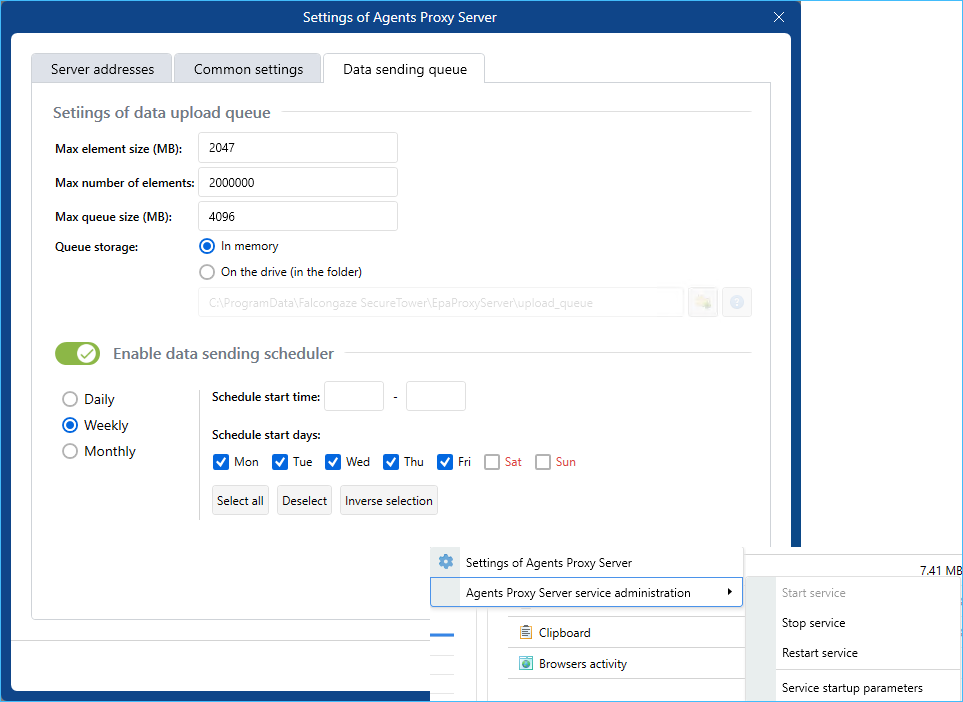
- You can install two or more agents proxy servers to balance load.
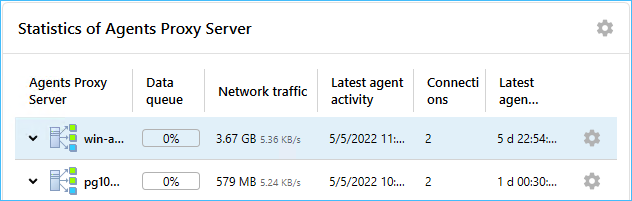
- Option to establish connection to the server using the server addresses list added. Agent keeps trying to establish connection using each specified address till the connection is established.
- Linux-based agent added
- Following distributives are supported: Ubuntu 20.04, Debian 11, Fedora 33, Rosa R12, Astra 1.70 and higher).
- Linux-based agent tasks: network traffic interception (SSL/TLS, SMTP, POP3, FTP, HTTP, XMPP, IMAP), keystroke logging, screen capturing, audit and monitoring of USB-devices.
- On the Image recognition server, the Tesseract image recognition plugin added
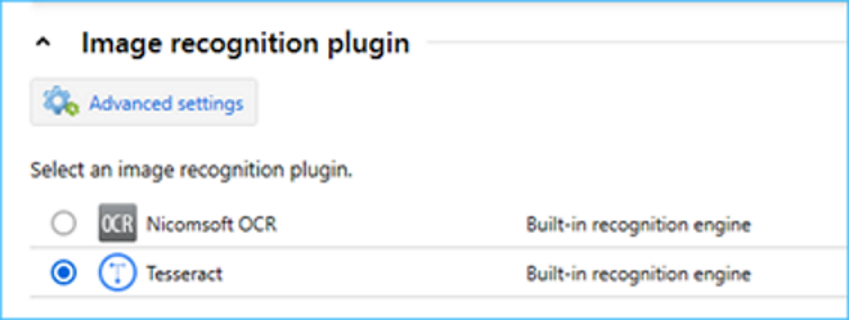
- The Tesseract image recognition plugin supports additional languages as well as multithread PDF-files through the integration with Ghostscript.
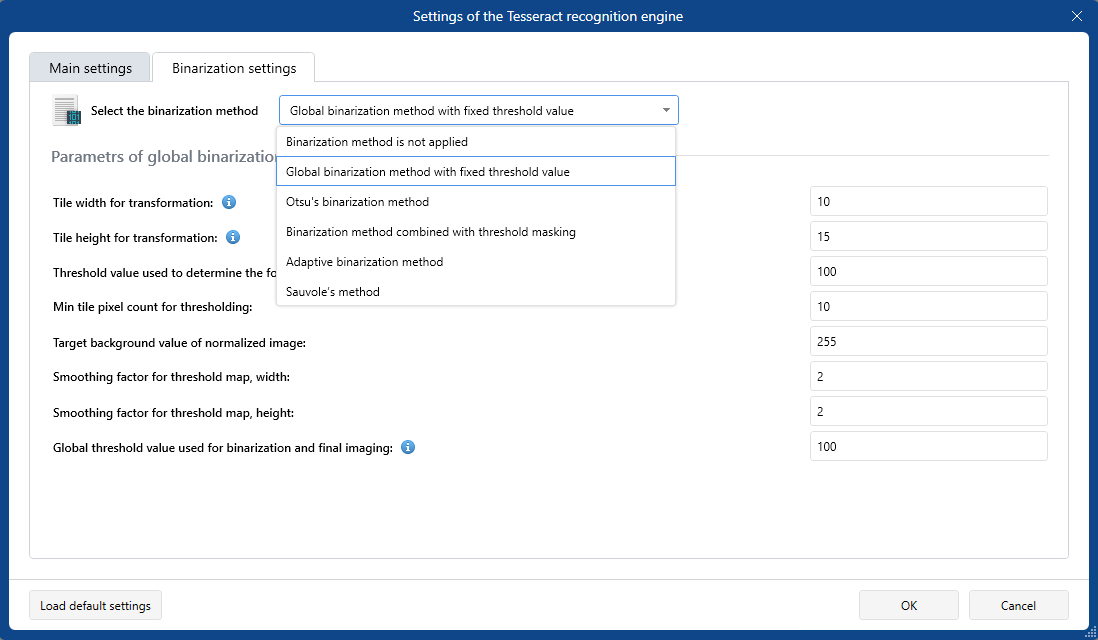
- For images with significant defects the binarization method as well as the fine binarization settings provided.
- Performance of image-document similarity detection module improved. CPU and RAM consumption reduced. Support of GIF-images added.
- Data protection capabilities during agent-server interaction extended
- To protect the agent from transferring data to illegitimate servers, the server authentication function implemented.
- To protect traffic between agents and servers from modification and forgery, digital signature of transmitted data added.
- To protect traffic between agents and servers from listening, data encryption added. The authenticated encryption algorithms used also protect data from modification and forgery.
- Option to establish agent-server connection using the TLS 1.3 protocol added. The protocol provides protection against connection to illegitimate servers, protection against listening, modification and forgery of data, hides the fact of the presence of network traffic of agents in the network.
- New options of intercepting data via the controlled messengers added
- Control of new version of Telegram web interface added.
- Control of messaging and file transfer in Zoom added.
- Control of voice calls in WhatsApp added.
- Data interception in Rocket.Chat and Zimbra added
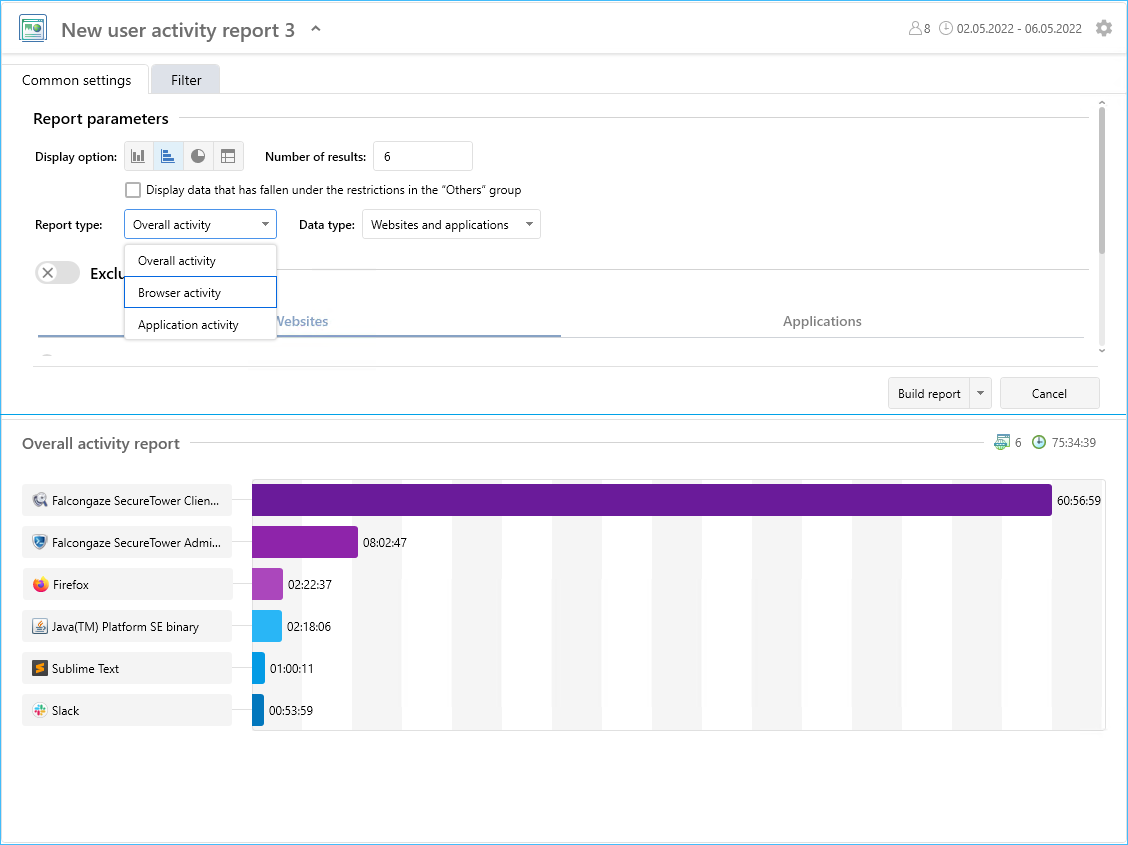
- New User activity report added
- New report type includes the total user activity, browser activity and apps activity.
- The Audit log module for investigations and security policies events allocated
- The Audit log module which comprises investigations and security policies events allocated.
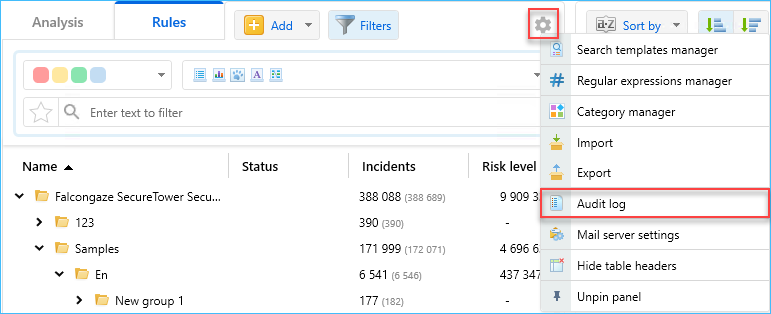
- Events description revised, usability improved.
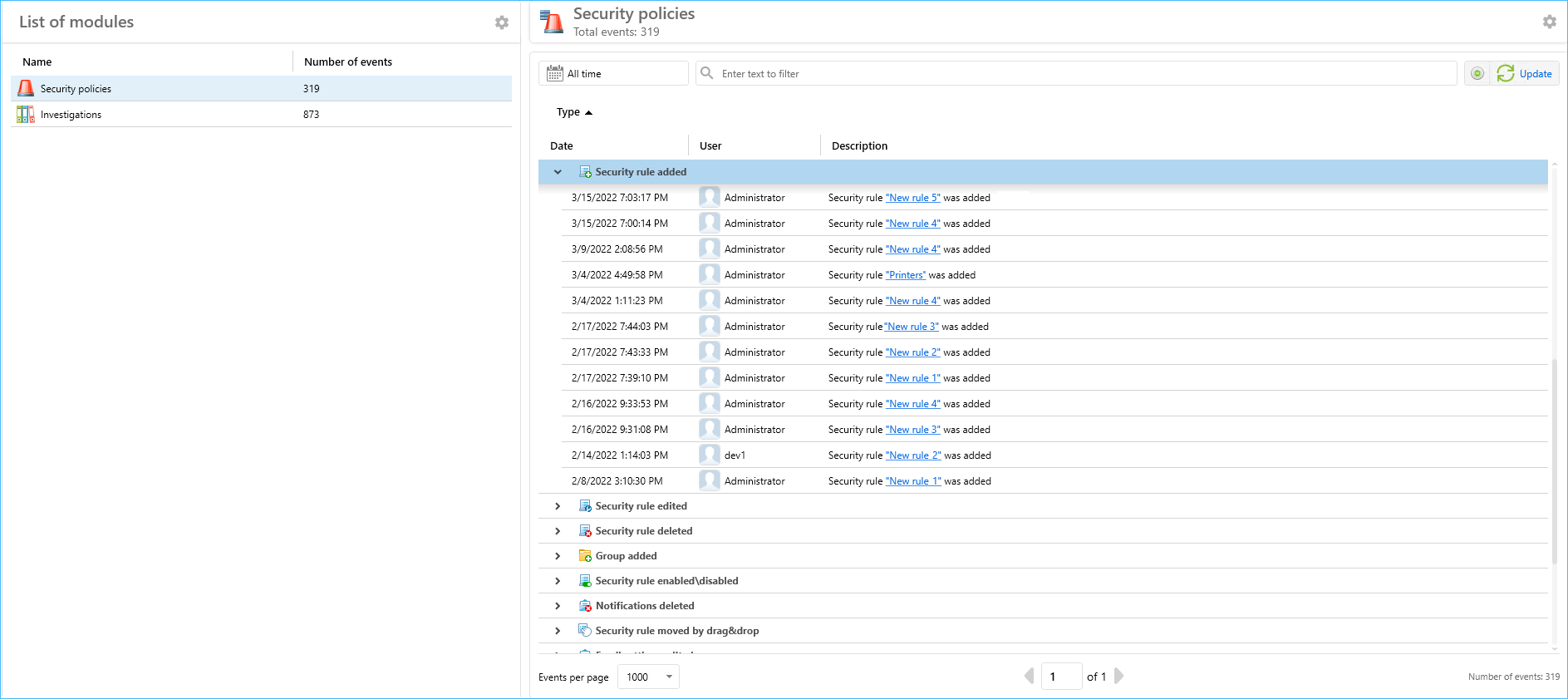
- Clipboard search possibilities extended: both Copy to clipboard and Paste from clipboard conditions supported
- In the Search conditions dropdown list the Clipboard item added. Additionally, user can select data type as well as pasting or copying operation.
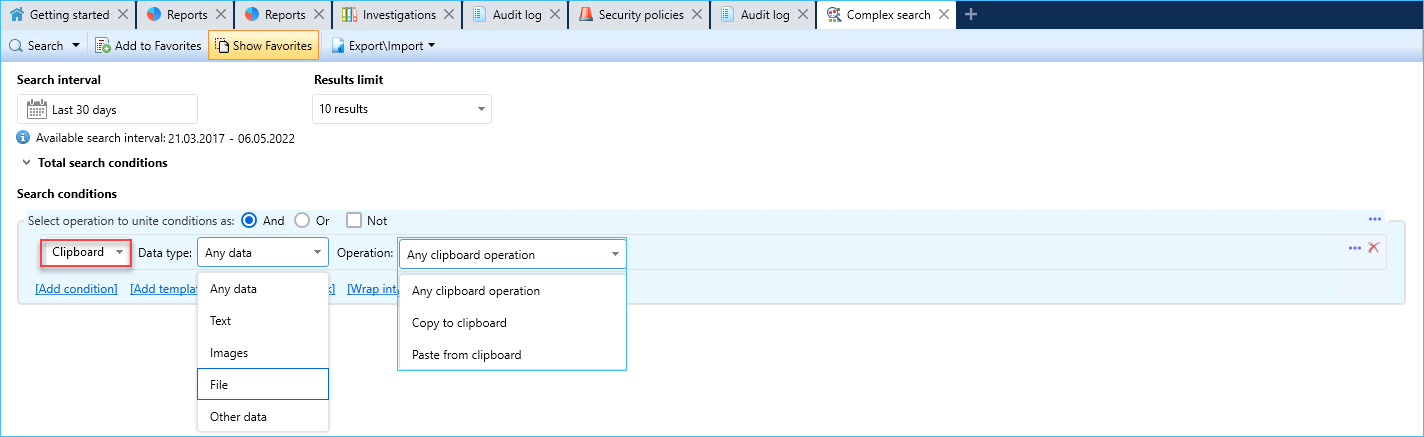
- In the complex user report, there are 2 counters for the Clipboard collection: Copy operations and Paste operations.
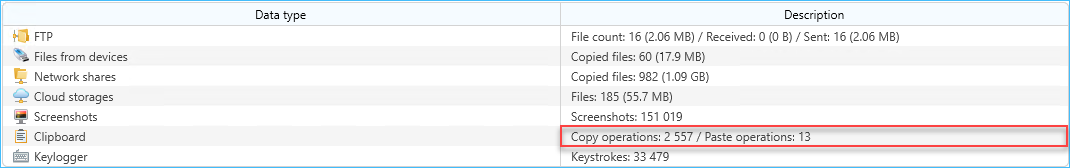
- In the consolidated report, total and daily average clipboard operations number counted. These parameters include all clipboard operations with all supported data types.
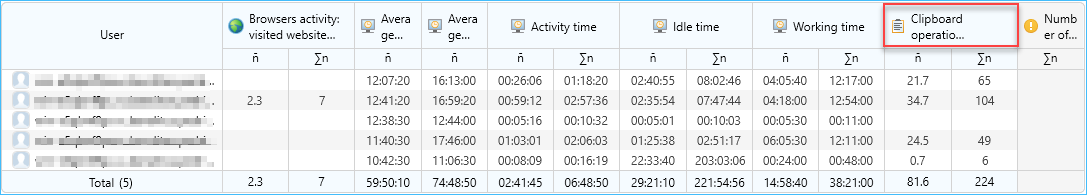
- Common parameter Number of clipboard operations added to the TOP-report. This parameter includes all clipboard operations with all supported data types.
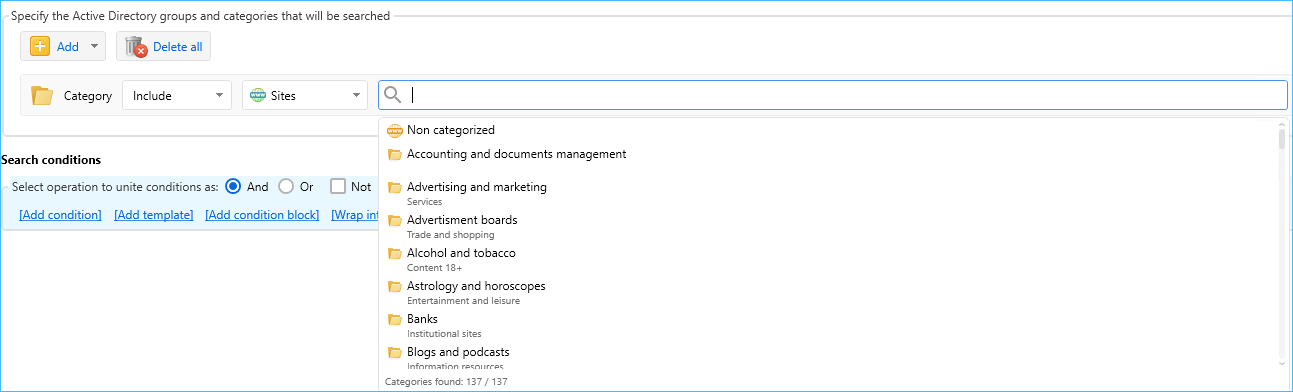
- Option to create search requests and security rules with account for the categorization service added
- When creating a search request, in the Common search conditions area, you can select a site or app category together with AD group to search within.
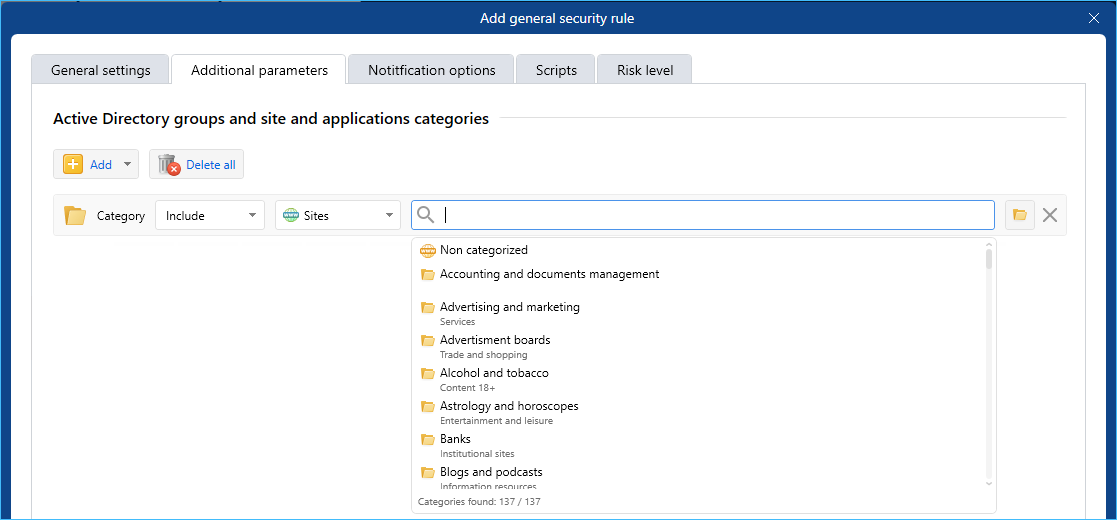
- When creating a security rule, on the Additional parameters tab, you can select a site or app category to consider during intercepted data analysis.
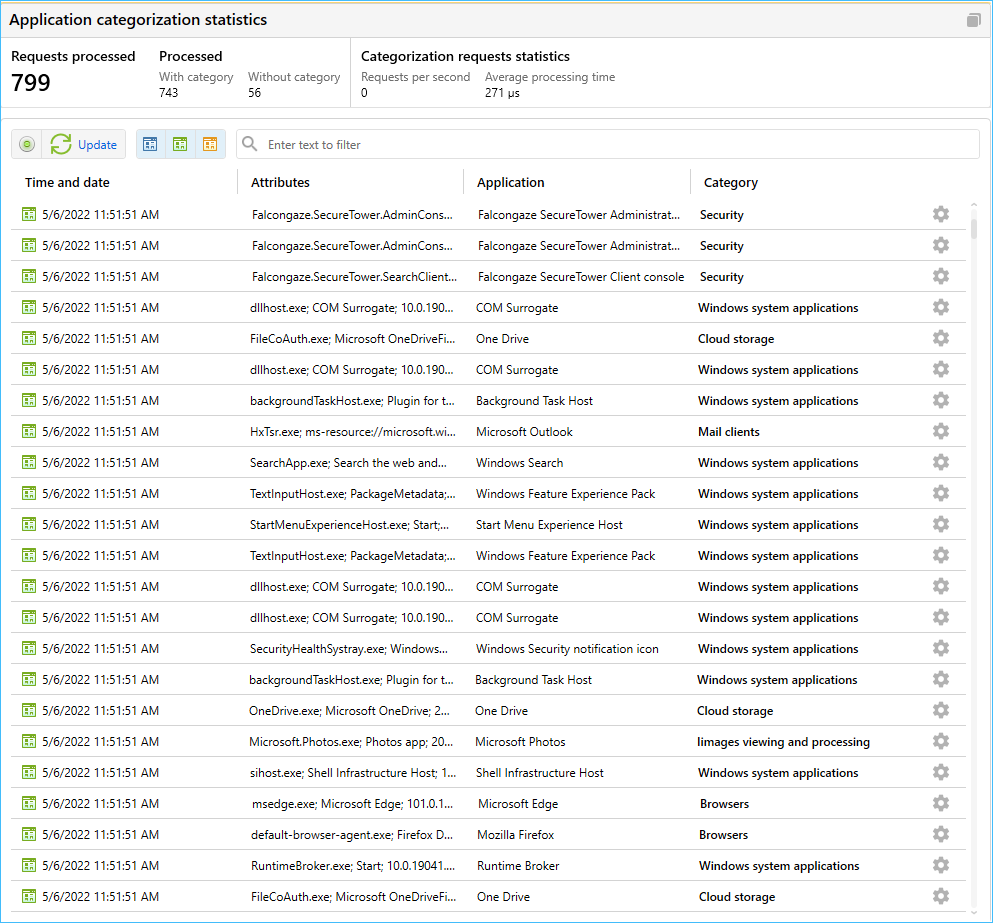
- Preset categories and dictionaries lists extended
- Currently, the categorization service includes appr. 22000 sites and 4000 apps. The lists are being constantly updated.
- Other system components are improved
- Option to comment security incidents added.
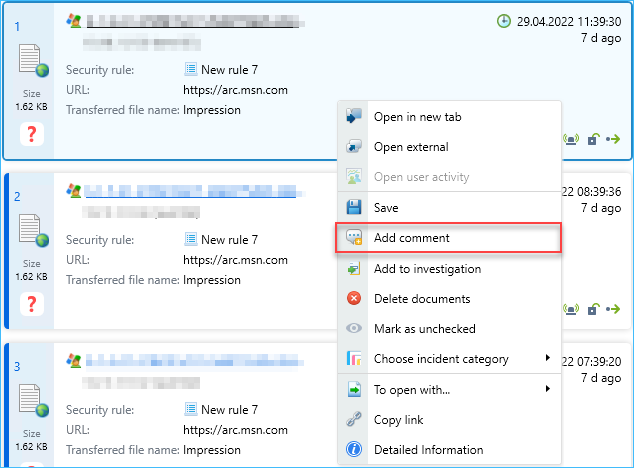
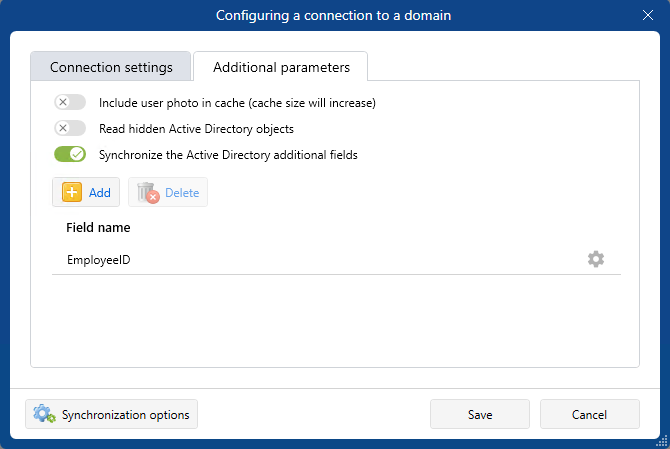
- On the Users and Privileges server, option to synchronize the additional Active directory fields added.
- Processing of Outlook calendar documents intercepted using the MAPI protocol, added.
- Occurrences count for blocking rules in the Agents and ICAP server modules added.
- Export of XLS files from the Client console is now possible without Microsoft Excel being installed.
- Option to add external files to the investigation using drag-and-drop added.
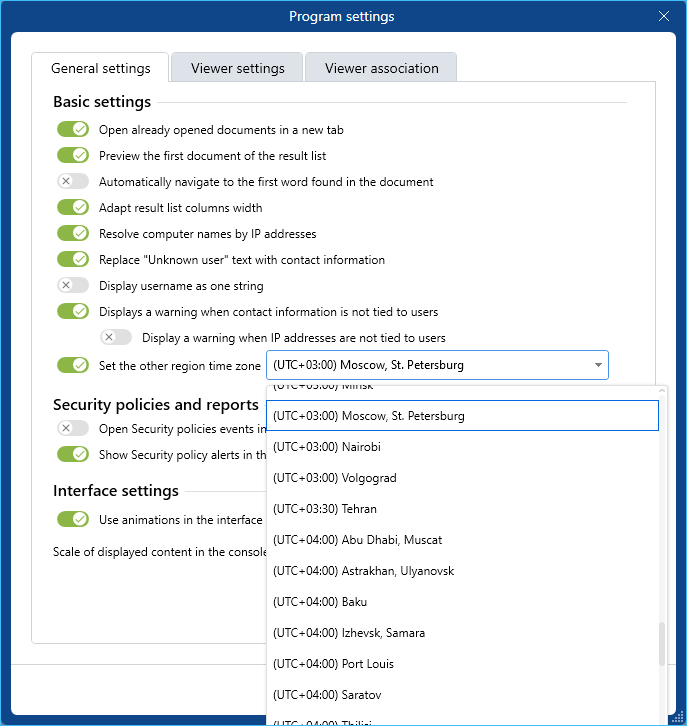
- Time zone setting option added in the Client console
- Option to select a time zone in the Client console added to correctly display all data received from the regions located in the other time zones.
- Option to set time for user session termination added
- When configuring user authorization, you can set the shutdown time after the session start.
- When setting up user authorization, you can set the end time of the session after N minutes of downtime.
