Çalışanlarınızın bilgisayarlarda nasıl çalıştığını kontrol edin

to understand how effectively employees work.

to see the full picture of the employees’ working day and optimize their work.

to identify fraudsters and unloyal employees.
SecureTower controls
and memorizes all the actions on employee’s computer
launch
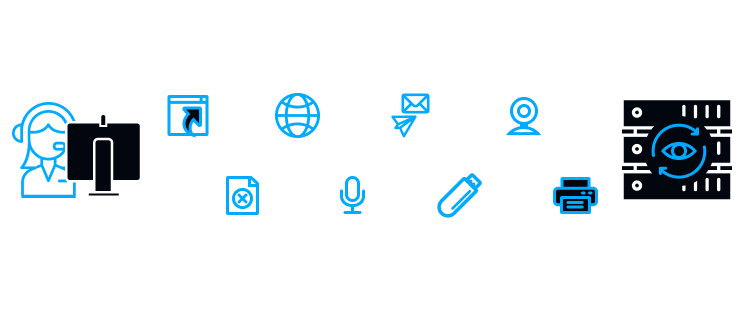
and deletion
of data
devices
connection
sent to print
Convenient and complete staff control
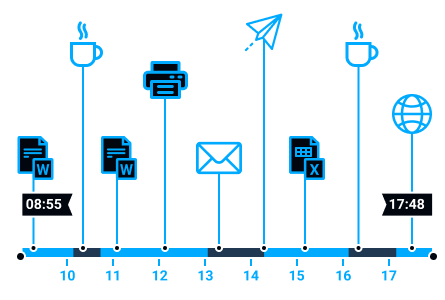
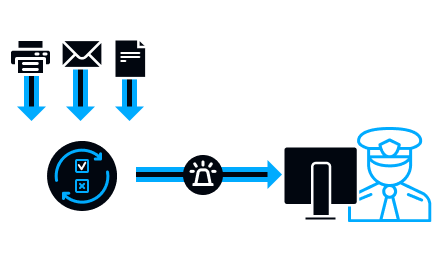
All the employee’s actions, communications and uploaded files are automatically analyzed for security rules violations and risk increase.
The security rules are preinstalled in the system, but there’s an option of creating custom ones for any business task.
If a violation is detected, the system immediately notifies the supervisor or security service./
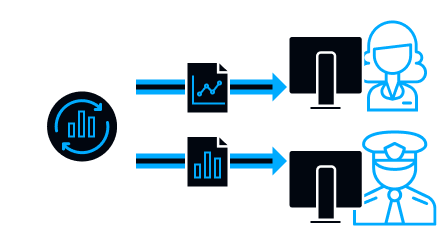
Fully customizable reports on security incidents and employees’ daily work are available for security officers and business unit managers.
Also, reports can be configured to be automatically generated on a schedule and sent to email.
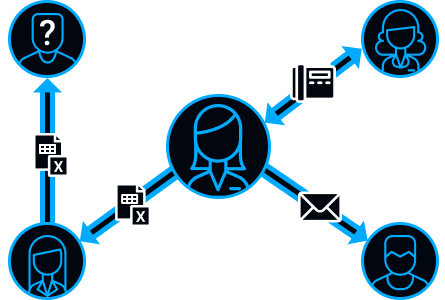
SecureTower uses a graph-analyzer to identify staff relationships, which has a profile for each employee, showing his communication with other people.
The profile contains email addresses, messenger names, social media accounts and other sites.
SecureTower remembers the addresses of all external contacts in order to identify external foes. Search for connections between groups of employees will find common external contacts.
This allows detecting an external intruder or, for example, a recruiter from competitors in a timely manner.
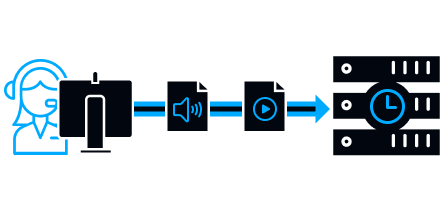
For effective investigation of breaches in SecureTower, you can connect to the employee’s computer, monitor its screen, record from a microphone or headset or record from a webcam.
In addition, recording can be set up for a specific event or at a specified time.