Աշխատակիցների մեղքով տվյալների խախտման պաշտպանություն
The information that is critical to business should not leave the company walls and access to it within the organization should be limited.
In SecureTower, complete control of corporate information is achieved by monitoring a maximum number of communication channels and data transfer protocols.
Full control of all communication channels

Visited sites


Cloud storages
Email


Social networks
IP telephony


Network storages
Network and local printers


Clipboard
USB devices


Messengers
FTP

Read more about monitored channels here
Automatic multi-parameter analysis
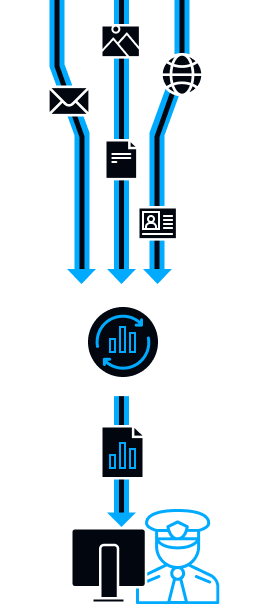
Content Analysis
Content analysis of files and documents:
- Analysis of text files and sent text (morphological features of the language are taken into account, text with grammatical errors or written in transliteration is analyzed)
- Image analysis (recognition of text in images, seals, stamps)
- Voice message and call analysis, speech recognition
- Analysis by added patterns/regular expressions (recognition of forwarded bank cards, passport photo, internal documents)
Statistical analysis
Quantitative recording of activities performed
Analysis of common connections between employees
Identification of information distribution channels
Analysis by digital fingerprints
Disguised file recognition
Search by hash functions
CAD file analysis
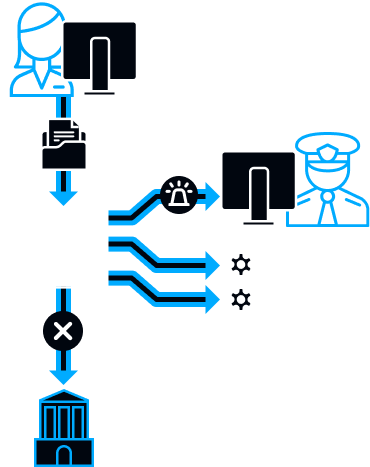
System triggering and notifications
After analysing the intercepted data, if there is a security breach, the system automatically alerts about the incident with all information about it.
Violating employee
Documents for official use
SecureTower server
Competitor company
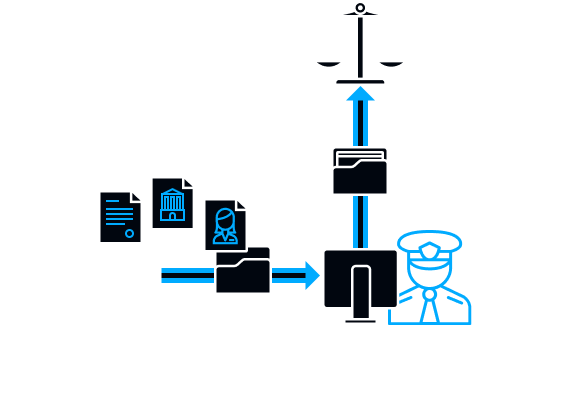
Incident investigation
When investigating incidents in SecureTower, cases are created, in which you can record the progress of the investigation, identify the persons involved, and after the investigation is completed, make a report to managers. The collected data can be used as evidence in court.