Top 5 Types of Data Your Competitors are After
In the majority of cases, information leakage is caused by staff negligence. It may seem that incidental disclosure cannot do much harm to the company, but in fact there are lots of cases when confidential information laid open to the public ruined the company’s reputation and even led to considerable financial damages.
But any accidental data loss cannot be compared with the damage caused by pointed attack of competitors. If the news of data leakage comes to light, it will be very difficult to avoid negative consequences from the fact of disclosure, and besides, the data itself can also bring the company into disrepute. But the most severe threat lies in the fact that data intended for internal use often costs more than all corporate assets put together.
Based on the data obtained with the help of SecureTower data leakage and staff activity control system, the specialists of Falcongaze analytical department conducted a survey into the types of information most valuable for competitors.
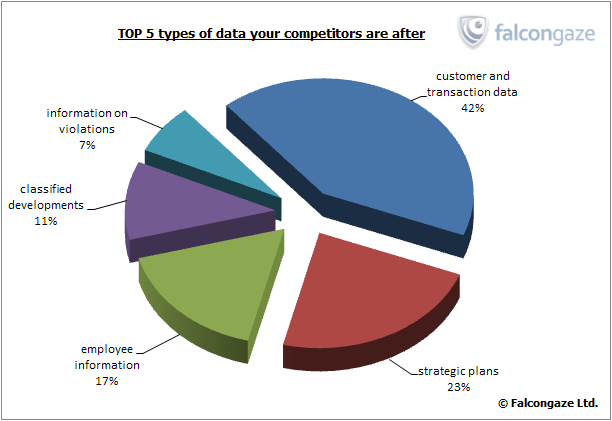
The specialists of Falcongaze found out that the most precious information for business rivals is the data on potential customers and transactions – both completed ones and those still on the way. Competitors revealed their interest in this kind of information in 42% of data security incidents.
The next issue is spying out the company’s plans regarding strategic and market development, new projects and products. Efforts to obtain this information were detected in 23% of incidents.
17% of industrial espionage attempts were targeted at confidential information about the employees of the company. Possession of such information gives a possibility to competitors to solicit key workers into their team. Besides, in many cases an employee who decides to leave, tends to take his client databases or even clients themselves to the competing supplier. Such behavior is motivated by the fact that the employee considers all his work on the previous workplace to be his own intellectual property, which gives him a right to use it even after he leaves the company. The information gathered by Falcongaze specialists shows that in the majority of cases the competitors try to obtain information about pay rates, bonuses and financial incentives.
11% of industrial espionage cases were attempts to sneak out rival’s developments and blueprints. Today the most valuable information of this type includes software code, drawings, algorithms – in general, all information which is relatively light-weight, but could cancel out a huge work carried out by the company.
Also, in some cases competitors purposefully try to get information on regulatory violations in the company and other facts that can be used to defame or blackmail the business rival. The employees of competing companies were interested in this data in 7% of the prevented incidents.
We can discuss long and hard whether it is possible to justify this manner of competition, but while you just keep complaining of unfair rivals, the rivals can strike you a very painful, if not fatal, blow. And the forces that may be used for development will have to be wasted on recovering from the heavy hook by the opponent. When it comes to intelligence, just as in the good old detective stories of outstanding espionage scandals, it is much more reasonable to think of adequate professional protection, rather than of mere revenge.

